AWS Roles, Policies, and Permissions
When you connect your AWS account to Panoptica – whether you’re launching a CloudFormation Stack via the Panoptica console or running a Terraform script – you will be defining the following roles and permissions.
Privileges
In order to integrate Panoptica with your AWS account, the user onboarding the account needs to have administrative rights to the AWS account.
Technically, it’s sufficient for the user launching the stack to be able to create/delete roles, create/delete policies, attach policies to roles, launch/delete stacks, and, if enabling serverless scans, create/delete Lambdas. But that’s pretty much the definition of the AdministratorAccess policy.
Roles
When you launch the CloudFormation stack (or run the Terraform script) you create a new IAM role in your account called SecurityAuditRole. Panoptica does not have access to make any changes to this roles after onboarding.
SecurityAuditRole is a role that has different policies attached to it that define what Panoptica can and cannot do. See Policies below for details. The full name is Panoptica-<onboarding_date>-<some random chars>-SecurityAuditRole-<more random chars>.
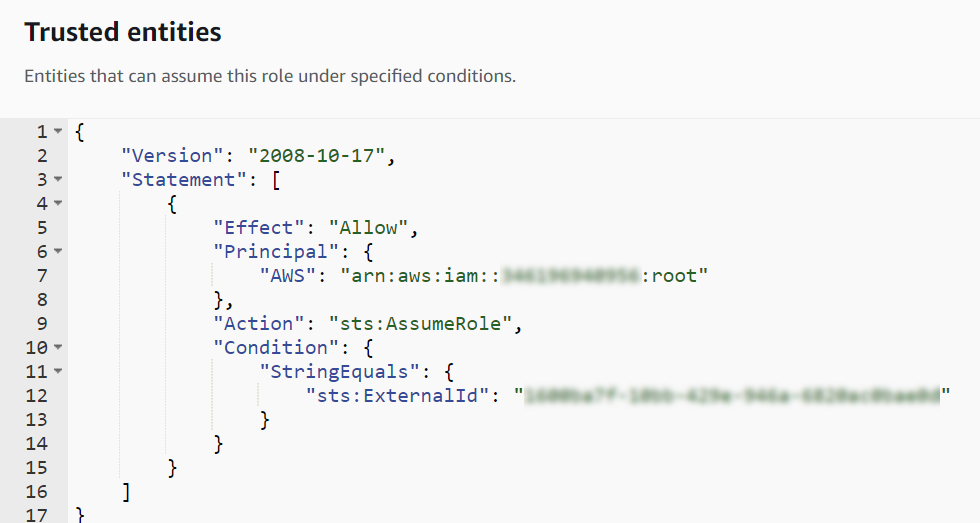
This role is assumed by a dedicated role in Panoptica’s AWS account (460146075389 for US and global customers; 365334924617 for EU customers) to facilitate the scans, according to a trust relationship. In AWS, a trust relationship defines what entities can assume a role that you've created. This Panoptica role is unique to your company, and is the only Panoptica resource with permissions to use the SecurityAuditRole. You can view the relationship in the Trust relationships tab of the SecurityAuditRole, under IAM > Roles.
Policies
Panoptica creates various policies at onboarding to enable the SecurityAuditRole to scan your AWS resources: three “AWS Managed” policies to enable standard CSPM security access, plus one customized policy to facilitate additional read-only access Panoptica requires. Additional policies may be created based on preferences you select at onboarding, such as CVE and Malware scanning, Serverless scanning, and/or Data scanning.
- AWSOrganizationsReadOnlyAccess (AWS Managed) - Provides read-only access to AWS Organizations.
- ViewOnlyAccess (AWS Managed) - Grants permissions to view resources and basic metadata across all AWS services.
- SecurityAudit (AWS Managed) - Grants access to read security configuration metadata.
- Panoptica-extendedAuditPermissions-policy (Customer inline) - This customized policy facilitates read-only access to resources not included in the standard policies, to support Panoptica features such as Compliance Framework, ECR scanning, and more. It also enables Panoptica to discover new AWS services as they come online.
Workload Scanning
If you enable CVE scanning of your workloads at onboarding, an additional policy is created for the SecurityAuditRole to support the scanning function, according to the scanning method you select.
Whether you select External scan or Internal scan, Panoptica takes snapshots of the EBS volumes and scans the snapshots, to minimize impact on your environment. The only difference is where the snapshots are scanned: in Panoptica’s AWS account (External), or in a local account you designate during onboarding (Internal).
panoptica-external-ec2-scan-policy (Customer inline)
This policy facilitates scanning snapshots in an account other than the current one. This could be Panoptica’s account ID, if you selected External scanning, or the scanner account ID you provided when onboarding, in the case of Internal scanning. Yes, even “Internal scanning” uses the external scan policy for any of your accounts that are not hosting the scan. Note that the snapshots are shared with the scanning account – whether external or internal – never copied or moved.
This JSON script defines the permissions that are included in this policy:
{
"Version": "2012-10-17",
"Statement":
[
{
"Action":
[
"ec2:CreateSnapshot"
],
"Resource":
[
"arn:aws:ec2:*:*:volume/*"
],
"Effect": "Allow",
"Sid": "SnapshotCreation"
},
{
"Action":
[
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Effect": "Allow",
"Sid": "TagSnapshot"
},
{
"Action":
[
"ec2:DeleteSnapshot",
"ec2:CopySnapshot",
"ec2:ModifySnapshotAttribute"
],
"Condition":
{
"ForAnyValue:StringLikeIfExists":
{
"ec2:ResourceTag/used_by": "panoptica - ec2 scan"
}
},
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Effect": "Allow",
"Sid": "SnapshotManagement"
},
{
"Action":
[
"kms:CreateGrant",
"kms:GenerateDataKeyWithoutPlaintext",
"kms:ReEncryptFrom",
"kms:ReEncryptTo",
"kms:RevokeGrant"
],
"Resource": "arn:aws:kms:*:*:key/*",
"Effect": "Allow",
"Sid": "KMSSnapshotManagement"
}
]
}
panoptica-internal-ec2-scan (Customer inline)
This policy facilitates hosting CVE scans for accounts you choose to scan using the Internal scan.
This JSON script defines the permissions that are included in this policy:
{
"Version": "2012-10-17",
"Statement":
[
{
"Action":
[
"ec2:CreateSnapshot"
],
"Resource":
[
"arn:aws:ec2:*:*:volume/*"
],
"Effect": "Allow",
"Sid": "SnapshotCreation"
},
{
"Action":
[
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Effect": "Allow",
"Sid": "TagSnapshot"
},
{
"Action":
[
"ec2:DeleteSnapshot",
"ec2:CopySnapshot",
"ec2:ModifySnapshotAttribute"
],
"Condition":
{
"ForAnyValue:StringLikeIfExists":
{
"ec2:ResourceTag/used_by": "panoptica - ec2 scan"
}
},
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Effect": "Allow",
"Sid": "SnapshotManagement"
},
{
"Action":
[
"kms:CreateGrant",
"kms:GenerateDataKeyWithoutPlaintext",
"kms:ReEncryptFrom",
"kms:ReEncryptTo",
"kms:RevokeGrant"
],
"Resource": "arn:aws:kms:*:*:key/*",
"Effect": "Allow",
"Sid": "KMSSnapshotManagement"
}
]
}{
"Version": "2012-10-17",
"Statement":
[
{
"Sid": "CreateKey",
"Effect": "Allow",
"Action":
[
"kms:CreateKey"
],
"Resource": "*",
"Condition":
{
"StringEquals":
{
"aws:ResourceTag/used_by": "panoptica - ec2 scan"
}
}
},
{
"Condition":
{
"StringEquals":
{
"ec2:ResourceTag/used_by": "panoptica - ec2 scan"
}
},
"Action":
[
"ec2:DeleteRoute",
"ec2:DeleteRouteTable",
"ec2:TerminateInstances",
"ec2:DeleteVolume",
"ec2:DeleteSnapshot",
"ec2:DeleteLaunchTemplate",
"ec2:DeleteSubnet",
"ec2:DeleteFleets",
"ec2:CancelSpotFleetRequests",
"ec2:DeleteNatGateway",
"ec2:DeleteVpc",
"ec2:DeleteKeyPair",
"ec2:DeleteInternetGateway",
"ec2:DetachInternetGateway",
"ec2:DeleteSecurityGroup"
],
"Resource":
[
"arn:aws:ec2:*:*:*"
],
"Effect": "Allow",
"Sid": "DeleteInfrastructure"
},
{
"Action":
[
"ec2:AuthorizeSecurityGroupIngress",
"ec2:CreateKeyPair",
"ec2:CreateNatGateway",
"ec2:CreateVpc",
"ec2:CreateRouteTable",
"ec2:AttachInternetGateway",
"ec2:AssociateRouteTable",
"ec2:CreateRoute",
"ec2:CreateSecurityGroup",
"ec2:CreateInternetGateway",
"ec2:CreateSubnet",
"ec2:ModifySubnetAttribute",
"ec2:CreateLaunchTemplate",
"ec2:AllocateAddress",
"ec2:DeleteLaunchTemplateVersions",
"ec2:CreateLaunchTemplateVersion",
"ec2:CreateSnapshot",
"ec2:CreateFleet",
"ec2:RunInstances",
"ec2:RequestSpotFleet",
"ec2:CreateTags",
"ec2:DisassociateRouteTable"
],
"Resource":
[
"arn:aws:ec2:*:*:*"
],
"Effect": "Allow",
"Sid": "CreateScanningInfrastructure"
},
{
"Action":
[
"iam:CreateInstanceProfile",
"iam:PassRole",
"iam:TagRole",
"iam:CreateRole",
"iam:PutRolePolicy",
"iam:AddRoleToInstanceProfile",
"iam:TagInstanceProfile",
"iam:AttachRolePolicy",
"iam:RemoveRoleFromInstanceProfile",
"iam:DeleteInstanceProfile",
"iam:DeleteRolePolicy",
"iam:DeleteRole"
],
"Resource":
[
"arn:aws:iam::*:instance-profile/panoptica-snap-scan",
"arn:aws:iam::*:role/panoptica-snap-scan"
],
"Effect": "Allow",
"Sid": "SetPermissions"
},
{
"Action": "iam:CreateServiceLinkedRole",
"Resource":
[
"arn:aws:iam::*:role/aws-service-role/spot.amazonaws.com/AWSServiceRoleForEC2Spot",
"arn:aws:iam::*:role/aws-service-role/spotfleet.amazonaws.com/AWSServiceRoleForEC2SpotFleet",
"arn:aws:iam::*:role/aws-service-role/ec2fleet.amazonaws.com/AWSServiceRoleForEC2Fleet"
],
"Effect": "Allow",
"Sid": "EnableRunningSpotFleets"
},
{
"Action":
[
"sts:DecodeAuthorizationMessage"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "VisualEditor1"
},
{
"Action":
[
"kms:CreateGrant",
"kms:RevokeGrant",
"kms:ReEncryptTo",
"kms:DescribeKey",
"kms:ReEncryptFrom",
"kms:GenerateDataKeyWithoutPlaintext",
"kms:TagResource",
"kms:ListResourceTags",
"kms:ListAliases",
"kms:CreateAlias"
],
"Resource":
[
"arn:aws:kms:*:*:*/*"
],
"Effect": "Allow",
"Sid": "KMSEncryptionManagement"
},
{
"Condition":
{
"StringEquals":
{
"aws:ResourceTag/used_by": "panoptica - ec2 scan"
}
},
"Action":
[
"kms:ScheduleKeyDeletion",
"kms:DeleteAlias"
],
"Resource": "arn:aws:kms:*:*:key/*",
"Effect": "Allow",
"Sid": "DeleteKey"
}
]
}
See AWS CVE Scanning - Details for more information on workload scanning.
Serverless Scanning

If you enable Serverless Scans at onboarding, two additional policies are created.
- AWSLambda_ReadOnlyAccess (AWS Managed) – This policy grants read-only access to AWS Lambda service, AWS Lambda console features, and other related AWS services.
- securecn-policy (Customer inline) – This policy facilitates security scanning of Lambda functions
We also create a Lambda function to perform the scan, and a dedicated role for this Lambda to use named LambdaVerifierRole.
This JSON script defines the permissions that are included in this policy:
{
"Version": "2012-10-17",
"Statement":
[
{
"Effect": "Allow",
"Action":
[
"lambda:InvokeFunction",
"lambda:InvokeAsync",
"lambda:UpdateFunctionCode",
"lambda:TagResource",
"lambda:UpdateFunctionConfiguration",
"lambda:UntagResource"
],
"Resource": "*",
"Condition":
{
"StringEquals":
{
"aws:ResourceTag/used_by": "panoptica - serverless scan"
}
}
}
]
}
Data Scanning
If you enable Data Scanning, a panoptica-data-scan policy is created to enable the automatic identification of sensitive data and secrets. The permissions included in this policy are:
- s3:GetObject – To retrieve objects from S3 buckets, including name, size, type, and the file itself
See Data Type Classification for more information on data scanning.
This JSON script defines the permissions that are included in this policy:
{
"PolicyName": "panoptica-data-scan",
"PolicyDocument":
{
"Version": "2012-10-17",
"Statement":
[
{
"Sid": "S3GetObject",
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "*"
}
]
}
}
NOTE:
Editing these policies and roles in any way will impact Panoptica’s ability to scan your resources and ensure your security posture. Please reach out to your Customer Success team if you have any questions.
AWS Organization
When onboarding an AWS Organization, the same roles and policies are created in a CloudFormation Stack in your root account. After you select the OUs to which you want to deploy the stack, AWS will deploy via StackSet to each account under the selected OUs.
Other Resources
The onboarding process also creates SNSPubResource, a notifier to inform the Panoptica backend when the onboarding is complete and scanning can begin.
Updated 7 months ago
