Exposing the API Controller for Trace Sources
When using gateway plugins to provide Trace Sources for Panoptica's API Security controller – such as AWS API Gateway, F5 BIG-IP, APIgee X, etc – the plugins need to be able to communicate with the controller, in order to provide visibility into your API traffic. When the gateways are external to the cluster where the API Security controller is running, the controller needs to be exposed externally through a publicly reachable URL.
Follow these steps to manually expose your API Security controller externally, so it can be reached by your external trace sources, and enable Panoptica to monitor run-time activity across your environment.
Controller installed in a cluster
A standard installation of the API Security controller in your cluster would not be exposed externally.
In this situation, when trying to attach an external trace source, the controller name would be grayed-out in the Attach Trace Source dialog box.
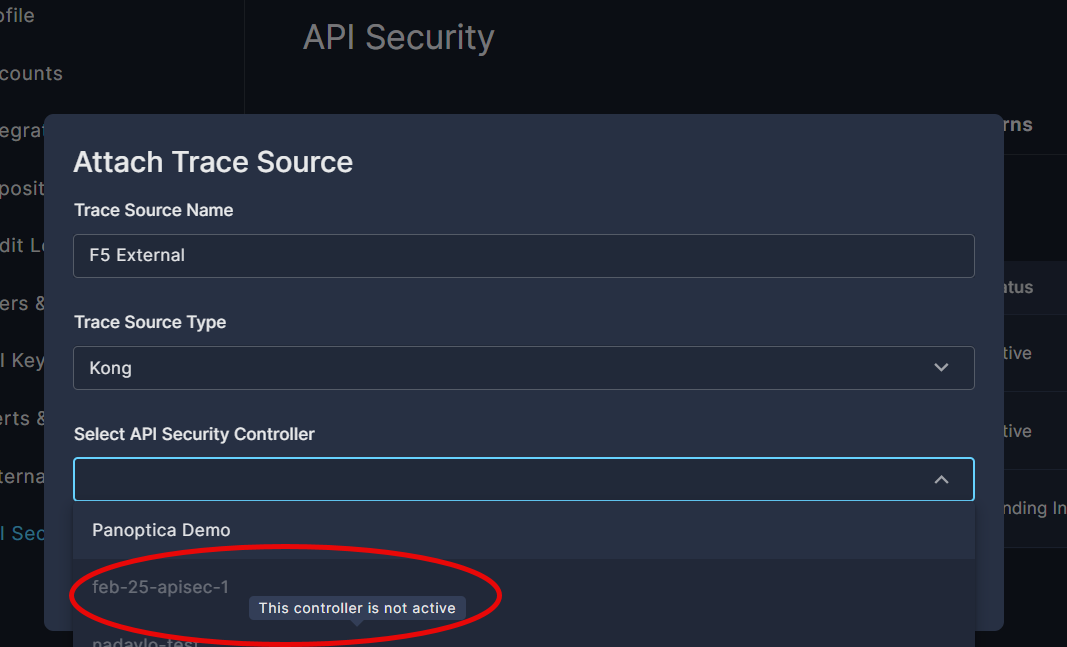
Expose API Security controller telemetry endpoint externally
To remedy this, you need to expose the controller telemetry endpoint externally. The endpoint to expose is the one corresponding to the following service:
$ kubectl -n panoptica get service panoptica-apisec-controller
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
panoptica-apisec-controller ClusterIP 10.8.1.77 <none> 80/TCP,443/TCP 20m
To achieve this, you need to provide:
- The external hostname where the service panoptica-apisec-controller is exposed
- A self-signed certificate used to expose the endpoint over TLS. (Optional)
In the absence of a self-signed certificate, Panoptica will assume that the certificate is a public one.
The external hostname and certificate are used to generate the appropriate configurations for the external trace sources (e.g. AWS GW) and need to be provided to the controller as described in the following section.
Provide external hostname and self-signed certificate to API Security controller
This section assumes that
- the external hostname is held in an environment variable named APISEC_EXTERNAL_HOSTNAME:
% echo ${APISEC_EXTERNAL_HOSTNAME}
my-apisec-contoller.acme.com
- the certificate is contained in a file named ca.crt:
% cat ca.crt
-----BEGIN CERTIFICATE-----
EXAMPLE/EXAMPLE/EXAMPLE/AUsJOotp3ux4uSUPuu+2pWcwDQYJKoZIhvcNAQEL
BQAwHzEdMBsGA1UEAwwUMzQuMTIxLjMwLjI0NC5uaXAuaW8wHhcNMjQwMjA2MTU0
OTAwWhcNMjYxMTI2MTU0OTAwWjAfMR0wGwYDVQQDDBQzNC4xMjEuMzAuMjQ0Lm5p
cC5pbzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMmminl4/bnv5/Cu
LXB5uKYe0DotWFKzt1IT5DKcSgA75mp3TPPbIyn2NtPGImSQMHdwTzX6oMhNSsRL
xt6BYpAh5J2ghBVBFNGMGeITVNQD89em67p4J/gUw8s4lKb8/Qt+tjvp9urHmDsn
AabGogtm9XeeBSPqa1rwHZexCV/Cn8O9oz/lMLsPqEghTPh5hfG+1JRLt2H4UoNC
OotGuRe/LgKJpL2yGwLRZ0PdraiaRS56zWCo63N4EZnLcAE2CVl/QTjtWKVKxVd0
r3ueeZfYx0/dk3gSMgx+0q103Us9LPYXLLewLhv7eAmXq/8Z4ljU9A/o0GYgOYYm
JrlVIWsCAwEAAaNCMEAwHwYDVR0RBBgwFoIUMzQuMTIxLjMwLjI0NC5uaXAuaW8w
HQYDVR0OBBYEFAyz8TGT71qoWOijy/QcEsG5Y+ICMA0GCSqGSIb3DQEBCwUAA4IB
AQAwCvaokkWO+Gw24BfXcATycFugqXX5qA6ZOtChsjBouqcA5RwfBn7GGNGs0TZY
wddvUr9Up2YP3pO8lnFy+g/Ykj90/KIyqGXXWeOF+kQX+M5F5kZRgyU5mkRyqTmE
+Uhr8jlLIB4KjHT36Iae2igcC0CGwKbZkhPkT5NIhPQRoexDMVtcTaOQc17gp4zG
uBRLbXJBbOH96NbhaqYgUd9DK9xb7QXT4I37w4/9fj9Y/cWloQT/381Z1e3vGa3Q
eDPX0JfgCxvc0uLIid3sLaPDBrwuLSyRIamVfRSbKZqRTRImqtAdqKnhoMa6R6GZ
yRhCgHOQo+LIhHkMB+rPwUWt
-----END CERTIFICATE-----
Run the following command:
kubectl -n panoptica set env deployment/panoptica-apisec-controller EXTERNAL_HOSTNAME=${APISEC_EXTERNAL_HOSTNAME} EXTERNAL_CERT="$(cat ./ca.crt)"
If successful the environment variable of the API Security Controller should be updated as follows:
aduminuc@ADUMINUC-M-59XM controller-manual-exposure % kubectl -n panoptica set env deployment/panoptica-apisec-controller --list
# Deployment panoptica-apisec-controller, container apisec-controller
...
...
EXTERNAL_CERT=-----BEGIN CERTIFICATE-----
EXAMPLE/EXAMPLE/EXAMPLE/AUsJOotp3ux4uSUPuu+2pWcwDQYJKoZIhvcNAQEL
BQAwHzEdMBsGA1UEAwwUMzQuMTIxLjMwLjI0NC5uaXAuaW8wHhcNMjQwMjA2MTU0
OTAwWhcNMjYxMTI2MTU0OTAwWjAfMR0wGwYDVQQDDBQzNC4xMjEuMzAuMjQ0Lm5p
cC5pbzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMmminl4/bnv5/Cu
LXB5uKYe0DotWFKzt1IT5DKcSgA75mp3TPPbIyn2NtPGImSQMHdwTzX6oMhNSsRL
xt6BYpAh5J2ghBVBFNGMGeITVNQD89em67p4J/gUw8s4lKb8/Qt+tjvp9urHmDsn
AabGogtm9XeeBSPqa1rwHZexCV/Cn8O9oz/lMLsPqEghTPh5hfG+1JRLt2H4UoNC
OotGuRe/LgKJpL2yGwLRZ0PdraiaRS56zWCo63N4EZnLcAE2CVl/QTjtWKVKxVd0
r3ueeZfYx0/dk3gSMgx+0q103Us9LPYXLLewLhv7eAmXq/8Z4ljU9A/o0GYgOYYm
JrlVIWsCAwEAAaNCMEAwHwYDVR0RBBgwFoIUMzQuMTIxLjMwLjI0NC5uaXAuaW8w
HQYDVR0OBBYEFAyz8TGT71qoWOijy/QcEsG5Y+ICMA0GCSqGSIb3DQEBCwUAA4IB
AQAwCvaokkWO+Gw24BfXcATycFugqXX5qA6ZOtChsjBouqcA5RwfBn7GGNGs0TZY
wddvUr9Up2YP3pO8lnFy+g/Ykj90/KIyqGXXWeOF+kQX+M5F5kZRgyU5mkRyqTmE
+Uhr8jlLIB4KjHT36Iae2igcC0CGwKbZkhPkT5NIhPQRoexDMVtcTaOQc17gp4zG
uBRLbXJBbOH96NbhaqYgUd9DK9xb7QXT4I37w4/9fj9Y/cWloQT/381Z1e3vGa3Q
eDPX0JfgCxvc0uLIid3sLaPDBrwuLSyRIamVfRSbKZqRTRImqtAdqKnhoMa6R6GZ
yRhCgHOQo+LIhHkMB+rPwUWt
-----END CERTIFICATE-----
EXTERNAL_HOSTNAME=my-apisec-contoller.acme.com
It is now now possible to attach the external trace source to this controller, as descriped in API Trace Sources.
Updated about 1 year ago
