SIEM Integration
Panoptica's SIEM integration enables you to export Security Findings and Attack Path information in JSON format. This allows you to periodically load all of the relevant SIEM results information into your SIEM system.
The results are generated upon each completed scan, excluding dismissed/snoozed data.
SIEM and Amazon S3 Buckets
To offload SIEM results to an Amazon S3 bucket, you first need to configure AWS S3 Bucket Integration.
Create Alert
To configure the SIEM exports, select Settings in the navigation pane, then Alerts & Notifications.
Click +Create Alert to open the pop-up form.
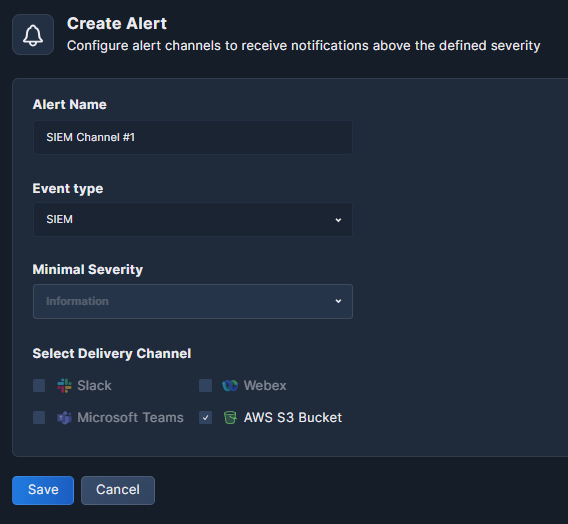
- Alert Name: Give your alert a logical name.
- Event Type: Selecting SIEM will enable selection of the AWS S3 Bucket delivery channel below.
Note that AWS S3 Bucket Integration must be configured first in order to receive SIEM results. - Minimal Severity: This field is disabled for SIEM results.
- Select Delivery Channel: Place a check mark beside Amazon S3 Bucket.
- Click Save.
SIEM JSON Schema
The following illustrates the SIEM JSON schema.
{
"type": "object",
"properties": {
"labels": {"type": "array"}, # The labels the main assets of the finding or attack paths has
"alert_id": {"type": "string"}, # Panoptica's Finding ID
"asset_id": {"type": "string"},# Your asset unique id
"provider": {# AWS, KUBE (Kubernetes), Azure, or GCP
"type": "string",
"enum": ["AWS","KUBE","AZURE","GCP"]
},
"resolved": {"type": "boolean"},# True for a resolved finding; otherwise, false.
"severity": {# Information, Low, Medium, High, or Critical (the calculated severity level)
"type": "string",
"enum": ["Information","Low", "Medium", "High", "Critical"]
},
"tenant_id": {"type":"string", "pattern": "^id"}, # Your tenant ID
"account_id": {# Comma-separated list of account IDs
"type": "string",
"maxLength": 50,
"minLength": 1
},
"description": {"type": "string"}, # Description of the security finding
"resource_type": {"type": "string", "enum": ["Compute", "Data", "Identity", "Network", "Service", "Storage"]},
"risk_params": {"type": "object", # This will appear only if the detection type is attack path.
"properties": {
"risk_score": {# The score calculated by Panoptica (0-100)
"type":"integer",
"maximum": 100,
"minimum": 0
},
"workload": {"$ref": "file://~/home/<user>/Desktop/SIEM_JSON_schemes/workloads.json"},
"risk_definitions": { "$ref": "file://~/home/<user>/Desktop/SIEM_JSON_schemes/risk_definitions.json"}
}},
"risk_category": {
"type": "string",
"enum":["Administrator Access Compromise", "Cross Account", "Data Exposure",
"Neglected Resource", "Privilege Escalation", "Risky Configurations", "Subdomain Takeover", "Vulnerable Public Workload"]},
"detection_type": {"type": "string", "enum": ["security_finding", "attack_path", "other"]},# Single-value field (detection type)
"attack_scenario": {"type": "string"}, # Name of the security finding
"related_resources": {"type": "array", "items": {"type": "array", "items": {"type": "string"}}},# Assets and resourced affected by the security finding
"detection_timestamp": {"type": "string","format": "date-time"},# Last seen timestamp
"first_seen_timestamp": {"type": "string","format": "date-time"}# Date when asset was first added
},
"if":
{
"properties": {
"detection_type": {"const":"attack_path"}
},
"required": ["detection_type"]
},
"then": {"required": ["risk_params"]}
}
Updated 6 months ago
