Policy Management (Preview)
The vast volume of security issues Panoptica reveals about your cloud environment can quickly lead to "information overload". Without a consistent methodology for applying security controls across your cloud resources, all the data in the world isn't going to prevent data breaches, unauthorized access, service disruptions, or worse.
Panoptica's Policy Management capabilities enable you to turn this information into action, by defining policies – composed of rules and frameworks – to manage and apply the data in a structured approach. Proper application of security policies can help monitor regulatory compliance, enforce internal policies, and respond effectively to emerging threats.
Policy Rules
The Policies tab is pre-loaded with hundreds of rules from across Panoptica's modules, exposing the built-in rules that Panoptica uses to secure your resources out-of-the-box. In addition to providing visibility into the Panoptica's security posture rules, this also enables you to identify content updates, by sorting the table according to the Last Updated field.
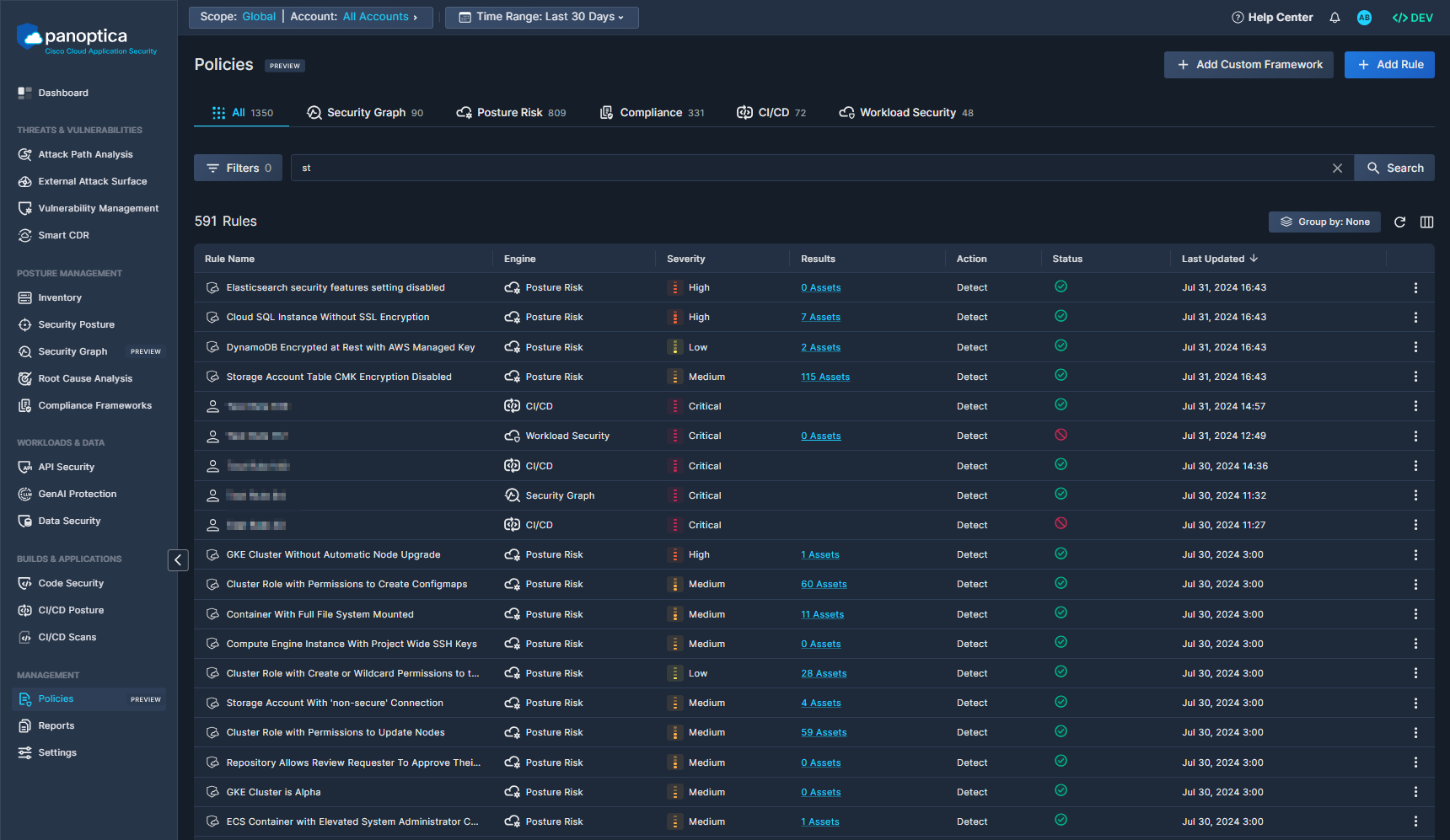
While you cannot edit Panoptica's built-in rules, you can customize their application by assigning them to custom frameworks and categories that you define.
You can also create or edit your own rules, to fit your needs. Custom rules appear alongside built-in rules in the Policies tab.
See Policy Rules for details regarding Panoptica's system rules, and instructions for creating and managing your own rules.
Custom Frameworks
A security framework is a structured set of controls designed to ensure that your information systems and processes meet security standards or compliance requirements specific to your industry, or internal policies specific to your organization. Panoptica's Compliance Framework is an example of applying industry-standardized frameworks to your cloud environment. Here is where you can create your own frameworks.
See Policy Frameworks for detailed instructions on creating and managing your own frameworks.
Updated 7 months ago
