Entitlement Management
Managing identities and access to IT resources has always been tricky. In the cloud, though, it's not just about which users or groups can access which files or applications. When services and resources themselves require access to other services and resource – across multiple cloud platforms, with constantly evolving services – it's beyond tricky. That's where Cloud Infrastructure Entitlement Management (CIEM) comes in.
Panoptica’s CIEM solution provides centralized visibility of user identities, access permissions, and entitlements across multiple cloud platforms, enabling you to detect and mitigate identity threats before they impact operations.
Permissive Access Detection
Effective permission analysis in CIEM refers to the process of evaluating and determining the actual permissions or access rights that users, roles, or services have within your cloud environment. This helps you adhere to the principle of least privilege by helping you understand the real-world access that an entity can exercise.
Panoptica examines the effective permissions in your cloud accounts, including AWS, Azure, and GCP, providing multi-cloud visibility into identity risks. After collecting the data, Panoptica then analyzes those permissions, identifying any risks that may result from overly permissive access to your cloud resources.
Any identity risks discovered are assigned severity levels, from Critical to Low:
| Severity | Relevant Risks | Use Cases |
|---|---|---|
| Critical | Admin Access High Data Access, High Management Access on Management Group Scope (like owner, full admin, write/*, etc..) | Unintended users holding admin permissions |
| High | IAM High Data Access, High Management Access on Subscription Scope (write/* on subscription, */delete on management group, roles with RBAC admin) | High management privileges granted to a wide scope |
| Medium | Service with wildcard Over permissive role like contributor | High data privileges granted to a wide scope |
| Low | Over permissive like */read | Wide services privileges granted to a wide scope |
Once identified, Panoptica then labels the assets according to the identity risks detected. These labels enable you to initiate simple workflows that focus on assets that might require more immediate attention.
The assets traits that are labeled are:
- Provider-based built-in users, roles and policies: Built-in Admin
- Identity with administrator privileges to one or more services: Shadow Admin
- Identity with privileges to manage permissions or resources: High Management Privileges
- Identity with privileges to access data: High Data Privileges
- Identity with access to multiple accounts or external accounts: Cross-Account
For example
One way to view Permissive Access risks in Panoptica is via Security Posture, located under Posture Management in the main navigation pane.
- Click Filters to filter the findings by Provider and Risk Category.
- Select whichever provider(s) you want, as well as Permissive Access under Risk Category.
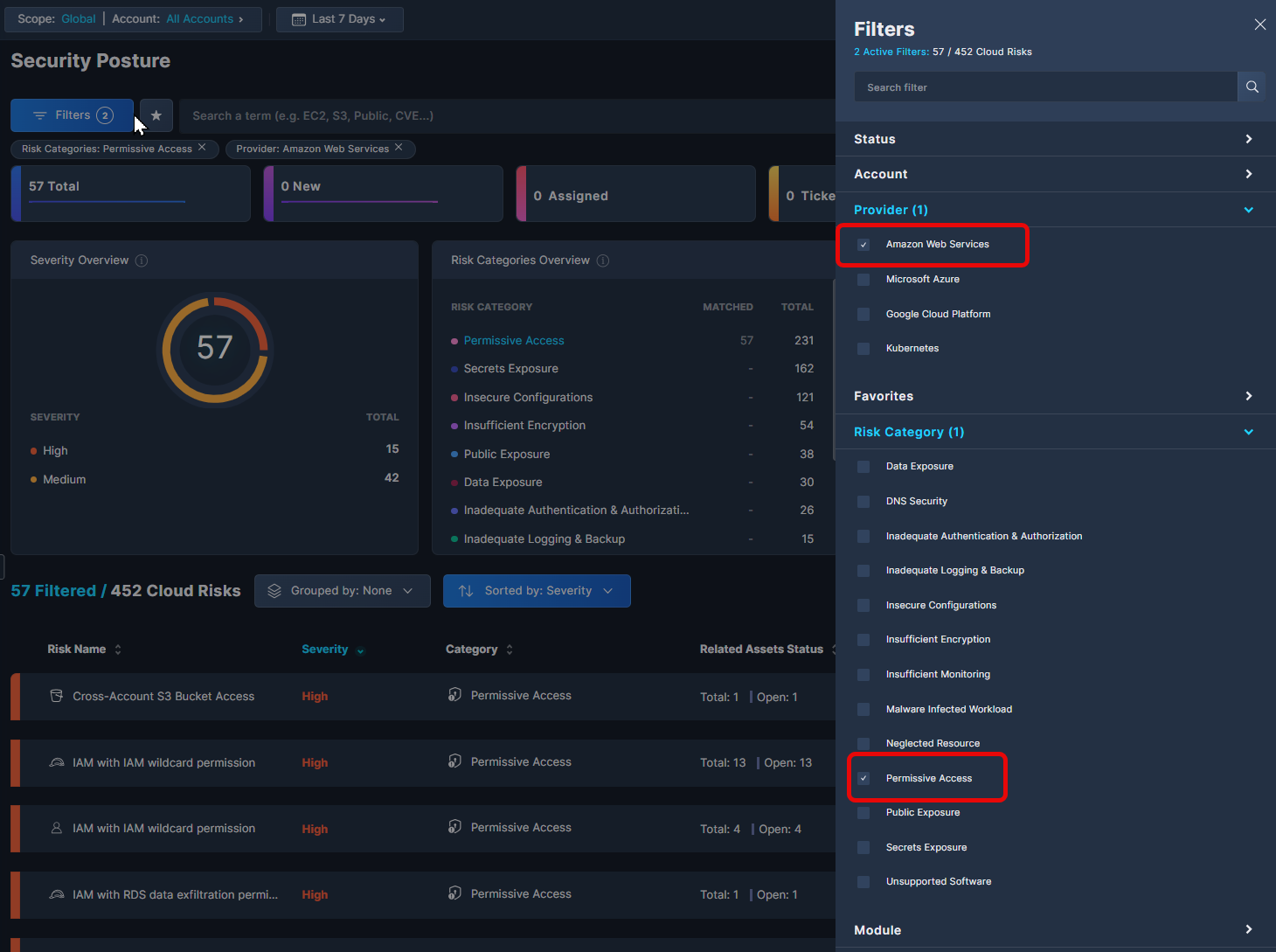
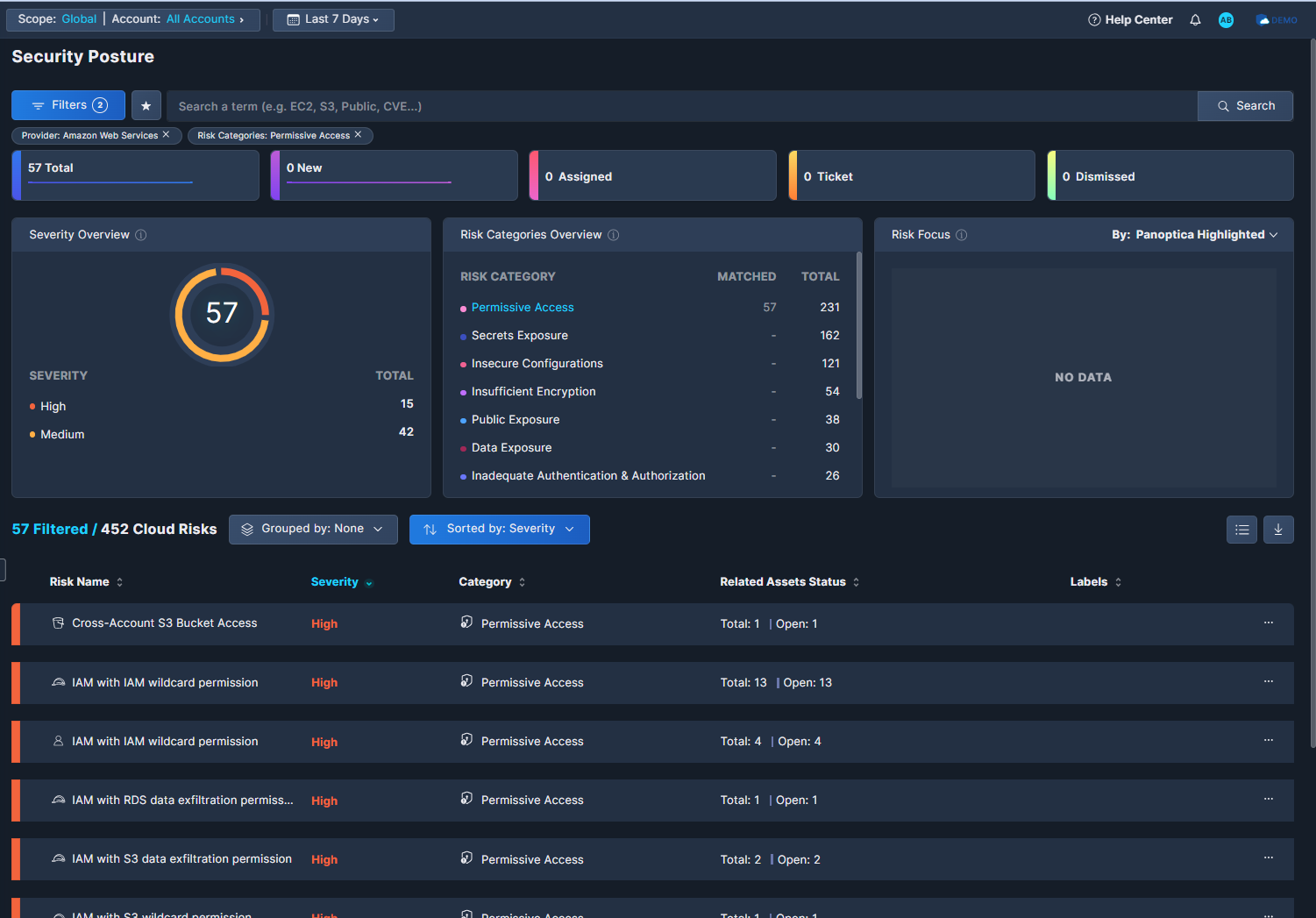
- These filters will return a list of all the Permissive Access risks Panoptica has discovered in that cloud environment, sorted by severity. You can change the sort order, or aggregate by any column.
- Click through to discover more details about any risk, see a list of the impacted assets, and view remediation steps.
Permission Usage Analysis
There's more to Entitlement Management than just blocking access. Some access is legitimate, as long as you adhere to the principal of least privilege. This risk analysis requires accurate assessment of which permissions are being used, and how. Panoptica analyzes your AWS CloudTrail data to provide visibility into how and when permissions are being utilized. Permission usage analysis is only available in AWS at the moment.
For example
To view Permission Usage data that Panoptica has collected from your AWS account, go to the Inventory tab under Posture Management in the main navigation pane.
Filter for AWS and Identity & Security, either by using the Filters, or by simply clicking those values in the Cloud Providers and Top Service Categories widgets, respectively.
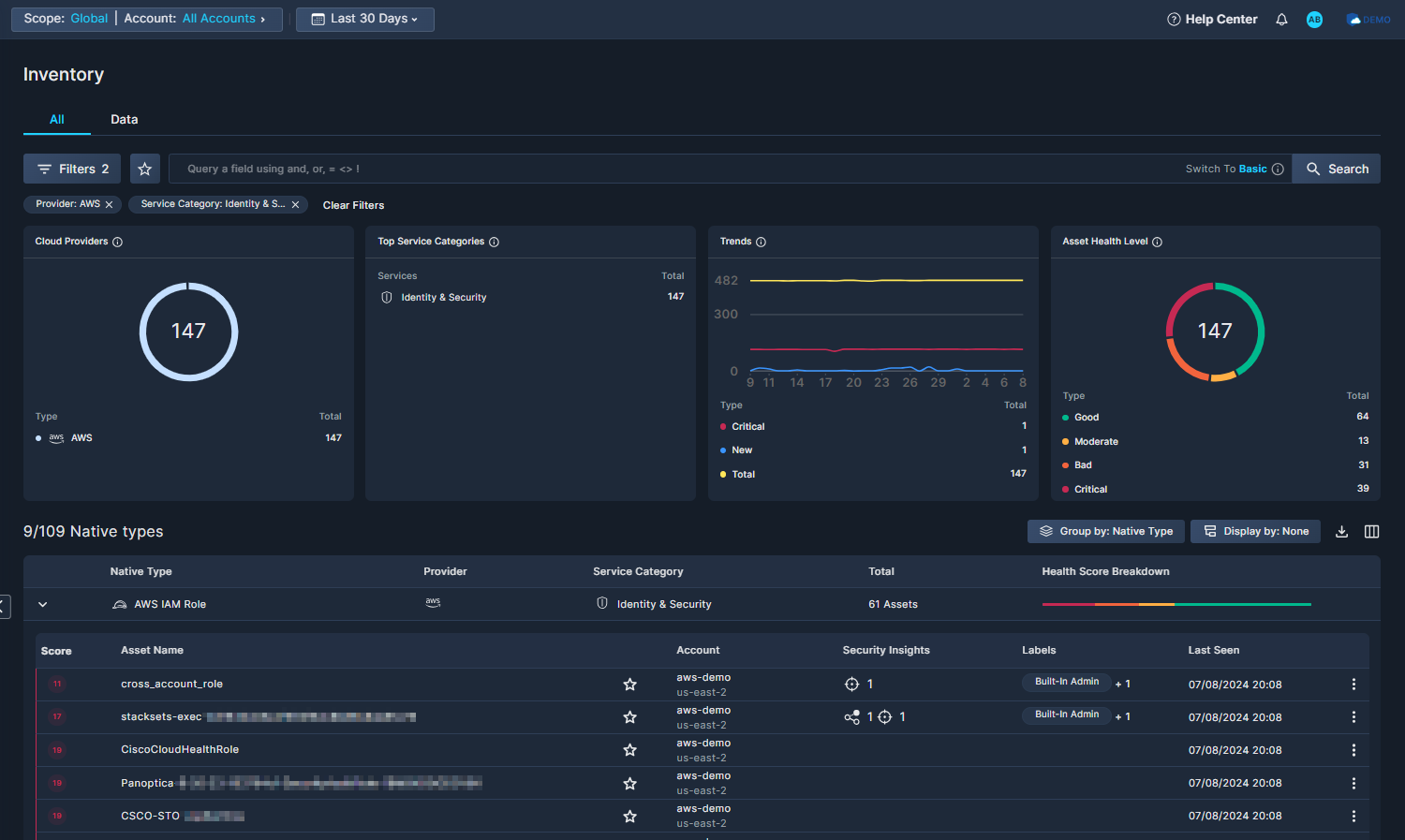
Click through to view the Asset Details, and go to the Permission Usage subtab.
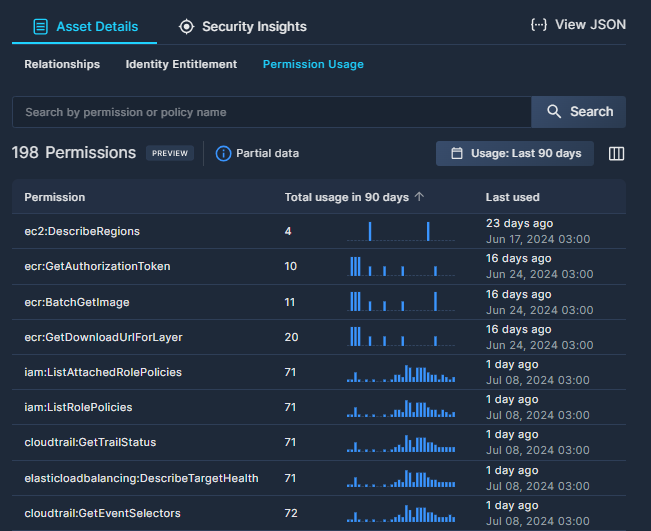
The Permission Usage subtab lists each of the permissions used by the role or user selected over a 90 day period. You can search for a specific permission, and change the time frame. The table lists how many times each permission has been used, a daily distribution of usage, and when it was last used. See the Asset Inventory documentation for further details.
Here are a few examples of how Permission Usage information can be used:
- Review permissions that haven’t been used much in the past 90 days and consider removing them.
- Analyze the information to validate permission usage before adjusting or removing permissions.
- Investigate anomalous permission usage.
Root Cause and Remediation
In some instances, the same root cause can be behind multiple security risks. Panoptica can help you identify those underlying root causes, and propose steps to remediate a number of risks with minimal action. One of the areas Panoptica's Root Cause Analysis addresses is Cloud Infrastructure Entitlement Management.
To view root causes in Panoptica, go to the Root Cause Analysis tab under Posture Management in the main navigation pane. There are two ways to focus on CIEM in Root Cause Analysis:
- Filter for Permissive Identity Object in the Root Cause Distribution graph
- Filter for Right-size IAM in the Remediation Focus Chart
Resolving the root causes listed in the filtered table below can improve your Panoptica health score. Click on each row to explore details about the root causes, and to discover remediation steps.
See the documentation on Root Cause Analysis for more information and details.
Updated 8 months ago
