Security Graph Rules
You can create your own rules in Panoptica to gain visibility into your organization's policies or compliance. Custom rules appear alongside built-in rules on the Policies page in the Panoptica console UI.
The Security Graph rule engine is based on the Query Builder at the heart of the Panoptica's Security Graph feature. This enables you to create custom rules that integrate your assets with security insights from across Panoptica's modules: CSPM, KSPM, API Security, and more.
Permissions required
Users must have an Owner or Ops role in Panoptica to create custom rules.
An Ops user can edit/delete custom rules that they created; an Owner can edit/delete any custom rule in your tenant. Panoptica system rules cannot be edited or deleted.
See User Management for details on User Roles.
Rule Creation
Click the + Add Rule button at the top of the Policies tab to start building your own custom policy rules, with actions, conditions, and operators.
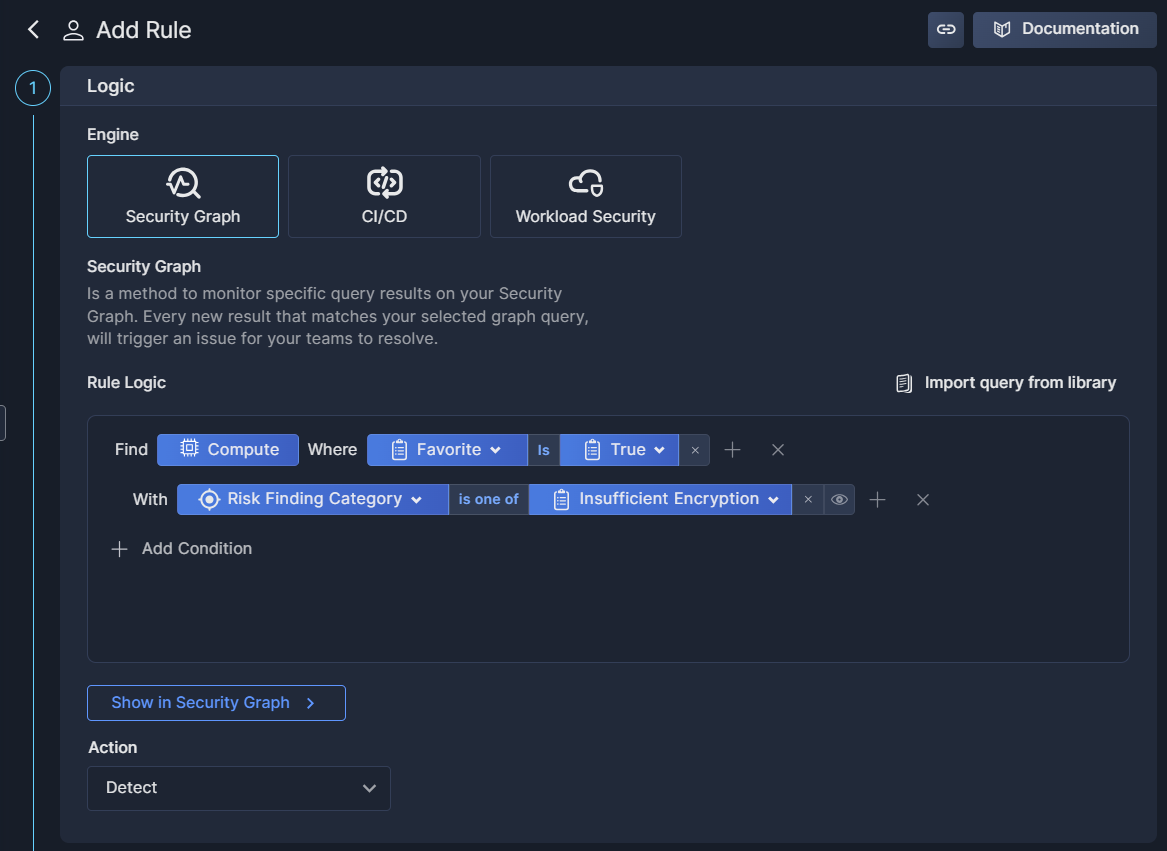
The Add Rule dialog box is where you define the rule logic, provide details about the rule, and define how and when it is executed.
Logic
The rule logic for the Security Graph engine uses Panoptica's Query Builder to create custom rules that integrate your assets with security insights from across Panoptica's modules: CSPM, KSPM, API Security, and more. Add advanced filters and relationship mapping between assets to customize rules on which to build your policies.
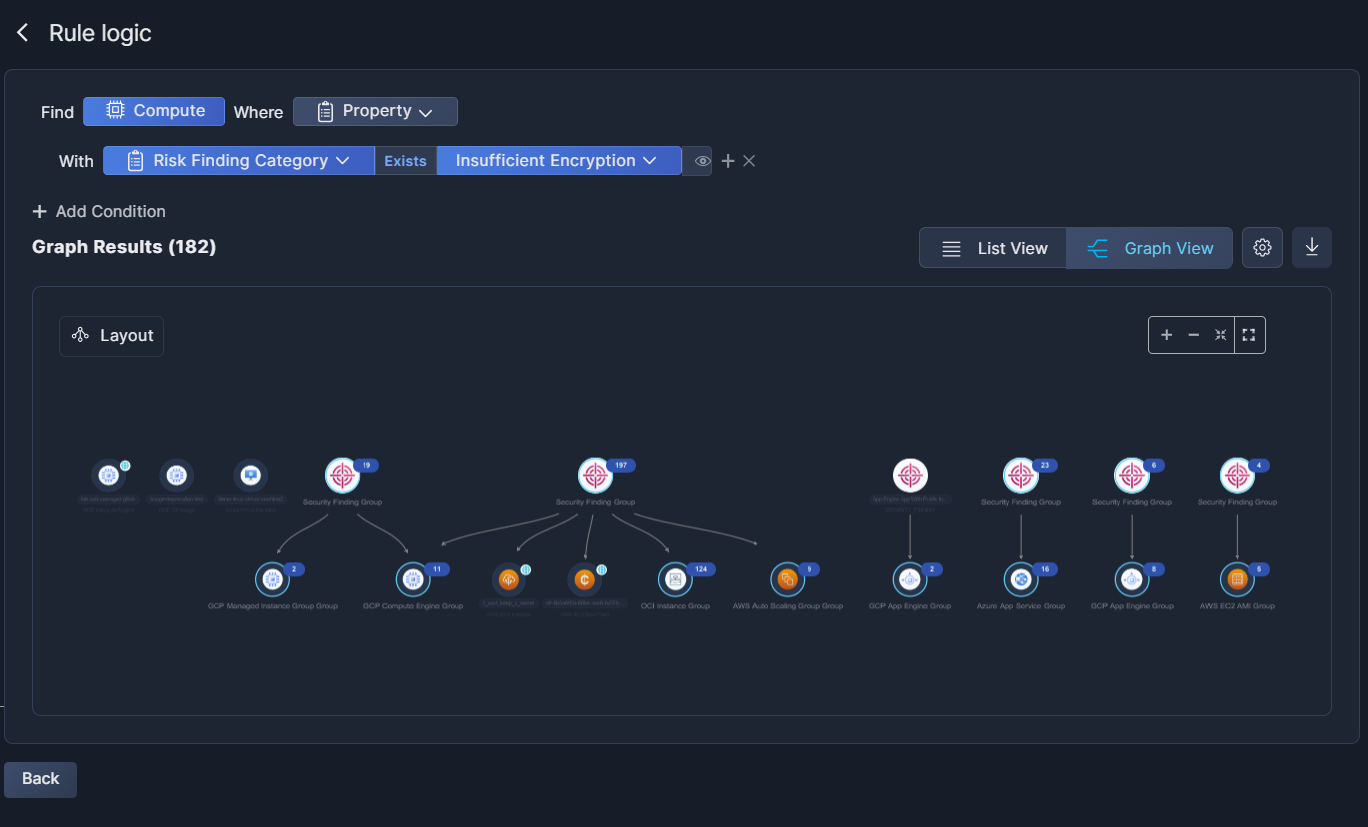
Start by clicking Asset or Security Insights, and selecting which you want to start with: one or more asset, or a Panoptica security insight. If you choose Assets, browse the list to find the Category, Asset Type, and/or Native Type (i.e. specific asset) you want to include in your query.
After selecting the base asset(s) for your query, you can filter the results according to specific criteria by clicking Properties. Alternatively, you can map linkage between different assets in your environment by clicking Relationship; or identify connections between your assets and Panoptica's Security Insights
The Security Insights option is where you correlate between the asset(s) in your query and Panoptica's security findings. By integrating Attack Paths or Risk Findings or Vulnerabilities that Panoptica has discovered with the assets you've selected, the Query Builder enables you to tailor the rule to your specific needs.
See the Security Graph Query Builder documentation for further details.
You can also import any queries you may have saved in the Query Library. See Import Query below for details.
To view the results of your Security Graph query in graphic form as you construct it, click Show in Security Graph.
Rule Info
This is the section where you provide details about the rule.
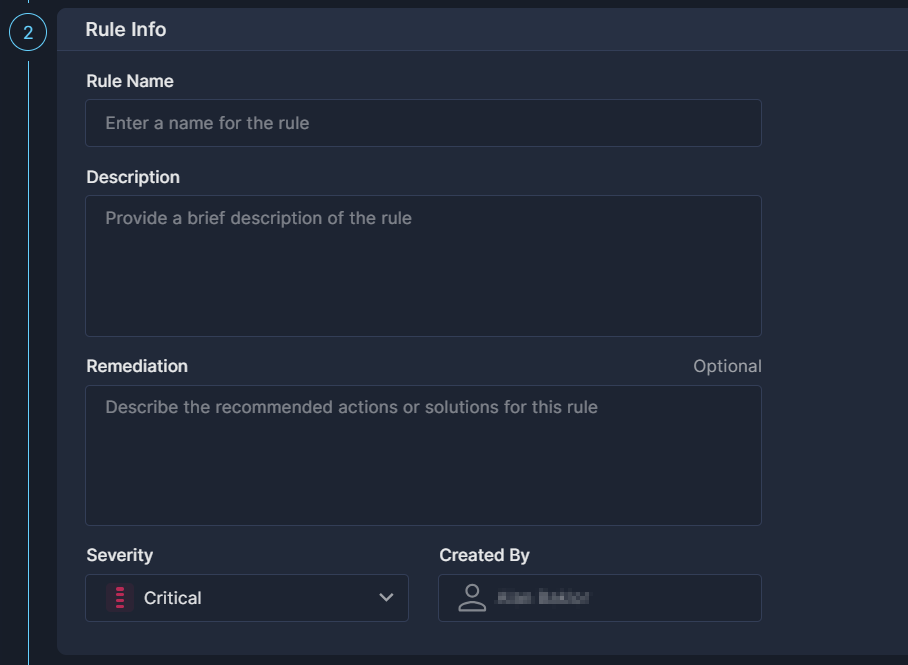
- Rule Name
A short textual name given to a rule. The name must be unique across your environment. - Description
A longer text that explains the motivation for this rule. This is also where you can store notes regarding the logic, execution, etc. - Remediation
Enter any remediation steps or actions that should be displayed when this policy is triggered. - Severity
The severity of the rule’s results. - Created by
This will always default to the logged-in user.
Rule Execution
Once the rule is defined, you need to decide how the new rule is to be applied to your environment.
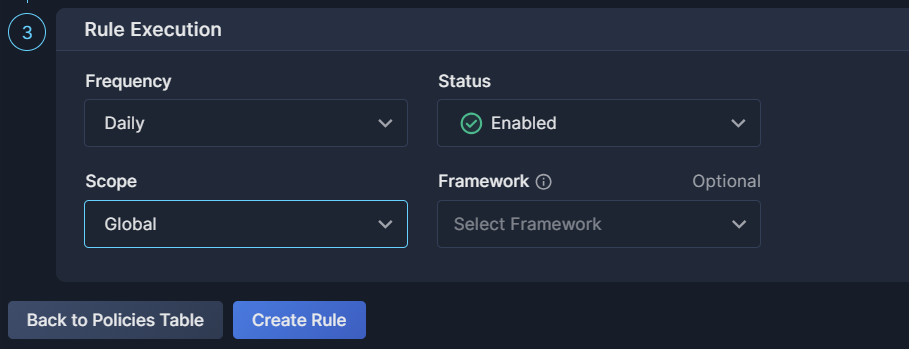
- Frequency
The interval at which this rule will be applied. This can vary according to the selected engine, and is aligned to Panoptica's scheduled scans. - Status
Select whether the rule should be Enabled or Disabled. - Scope
The selection of accounts and/or users on which this rule is to be run.
Note that policy rules are filtered by scope. If you create a rule in the Global scope, it will not be visible if you set the Top Bar Filter to another scope, and vice versa. See Scope Management for details on defining scopes. - Framework
Select the frameworks and/or categories that this rule is to be associated with. You can attach the rule to more than one custom framework, but you cannot associate with built-in frameworks defined by the system.
Don't forget to click Create Rule when you're finished defining your Security Graph custom rule.
Import Query
If you've already created Security Graph queries, and saved them in the Query Library, you do not need to reinvent the wheel. You can simply import those queries into the Add Rule dialog box to create a new Security Graph rule based on an existing query.
-
With Security Graph selected in the Add Rule dialog box, click Import query from library
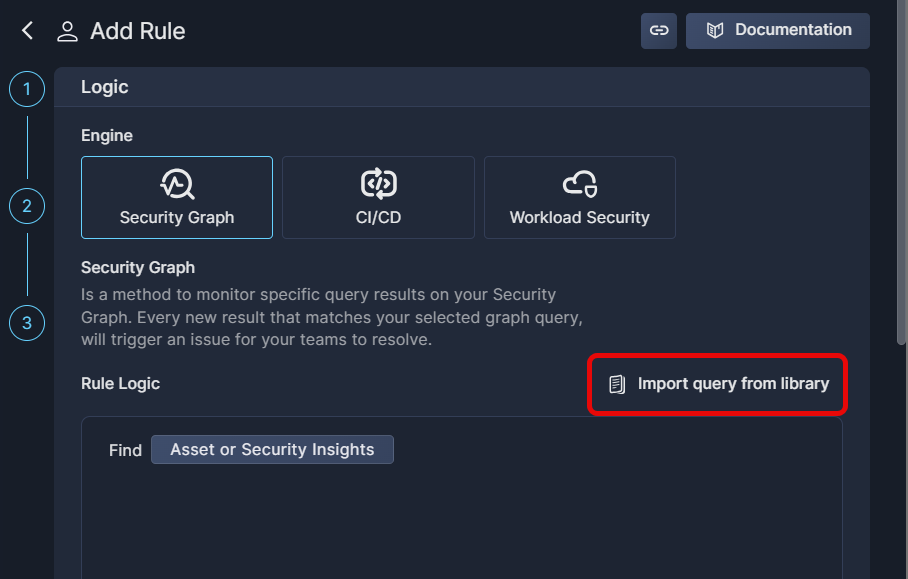
-
This will pop up a dialog box from which you can select any of the queries saved in the Query Library.
Use the Search bar and/or the Category list to narrow the selection.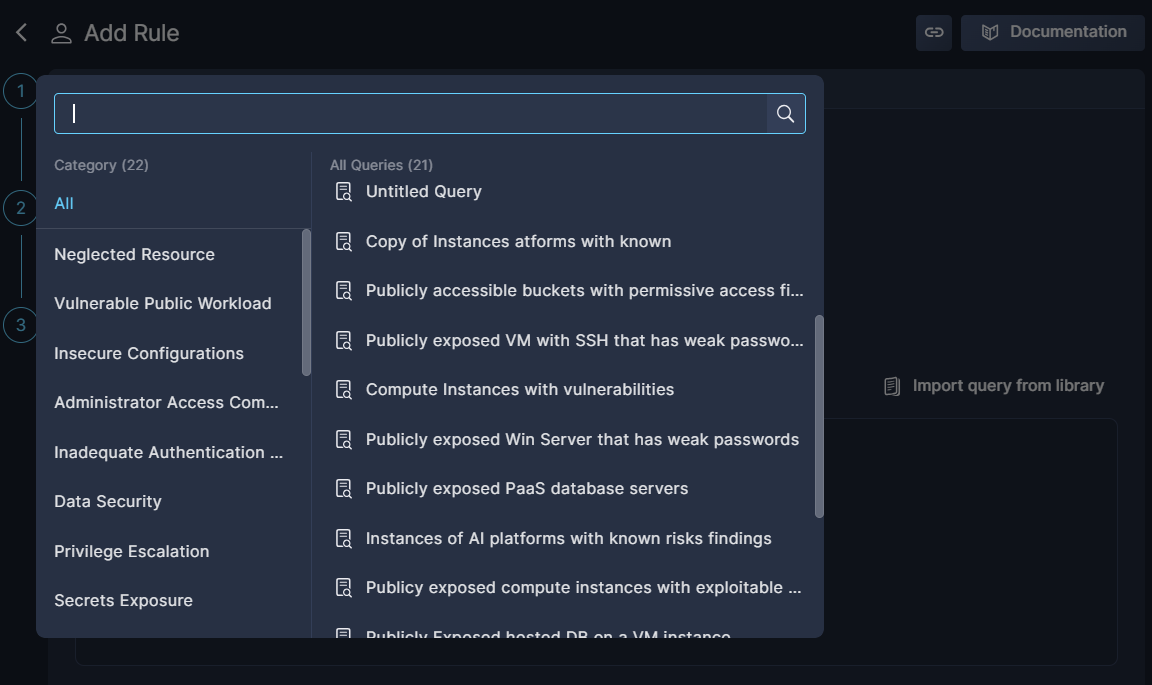
-
Once imported, review the Rule Logic, Rule Info, and Rule Execution, just like you would for a new rule.
-
Click Create Rule to save a new Security Graph rule based on a saved query.
Use Cases
There are myriad ways you can apply policies based on Security Graph rules to enhance your organizations security posture. Here are two primary use cases
Toxic combination
By selecting a specific type of asset, combined with some relationship, you can use the security insight to discover assets having many types of findings together. Use the ‘include all’ operator to look for assets having all the specified findings, and not just one of them. This type of query can help you discover assets combinations that could pose a risk to your environment.
Such a query could look something like this:
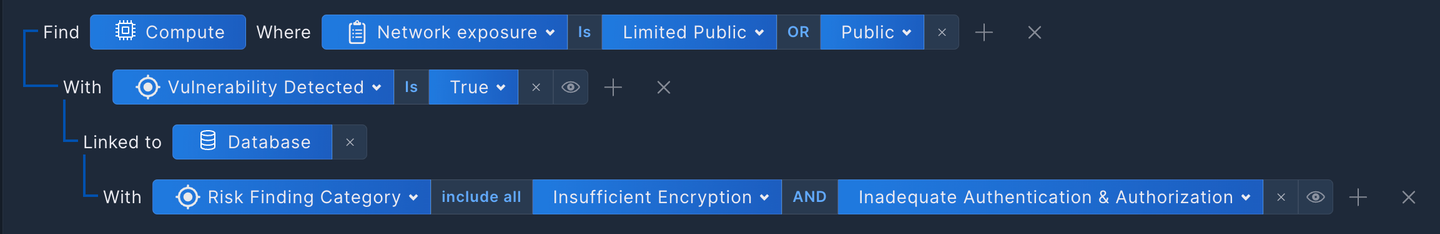
This query will identify publicly exposed compute assets with a vulnerability, which are linked to a database with insufficient encryption and inadequate authentication and authorization. The combination of exposed compute assets with vulnerabilities and an insufficiently protected database could be toxic.
Organization custom policies
You can apply conditions on asset names or tags to capture unintended behaviors. For example, if your organization has a policy to use specific tags on compute instances or identities, you could build queries that will look for those tags.
Such a query could look something like this:
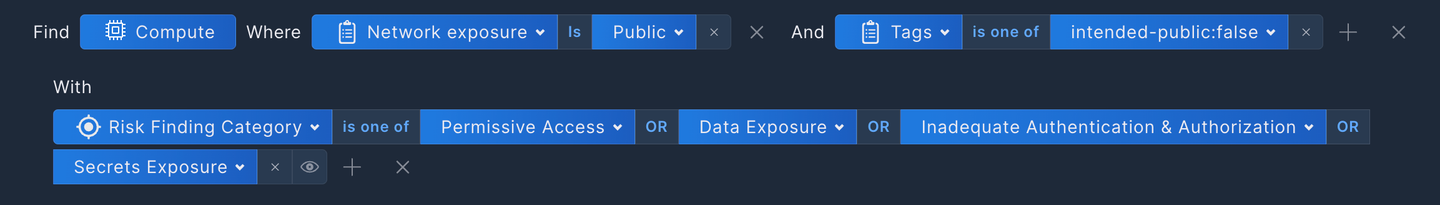
This query will identify publicly exposed compute assets with tags that should not be public with one of the following risk findings: Permissive Access, Data Exposure, Inadequate Authentication and Authorization, or Secrets Exposure.
Updated 7 months ago
