CVE Scoring and Prioritization
The vast quantity of CVEs discovered by Panoptica can be paralyzing without actionable context. That context is provided by the range of scanning tools and threat intelligence feeds Panoptica employs to provide better insight into those vulnerabilities, as well as automated prioritization of the most potentially impactful CVEs.
CVE Scores
There are a number of metrics available to score and rate vulnerabilities. Panoptica applies industry-leading tools, from the standard CVSS to Cisco's own Security Risk Score and EPSS. You can view these scores in the relevant columns of the Vulnerability Management table.
- CVSS Score: The Common Vulnerability Scoring System (CVSS) provides standardized numerical values that represent the severity of security vulnerabilities. The CVSS database is maintained by the US National Institute of Standards and Technology (NIST).
- EPSS Score %: Cisco's "Exploit Prediction Scoring System" (EPSS) estimates the probability that a vulnerability will be exploited in the wild in the next 30 days, on a scale from 0 to 100%. See EPSS and Its Role in Cisco Vulnerability Management Risk Scoring for more information.
- Cisco Security Risk Score: Cisco Vulnerability Management (formerly Kenna.VM) is a risk-based vulnerability management solution that uses data science and machine learning algorithms to assign a dynamic real-time security score to vulnerabilities, displayed on a scale from 0 to 100.
- Vulnerability Risks
- Publicly Exposed: To obtain a comprehensive view of all publicly-exposed services and assets in your environment, Panoptica employs Shodan.
- Exploitable: Shodan also identifies exploitable vulnerabilities.
- Thread Trends: The Known Exploited Vulnerabilities catalog (CISA KEV) is the authoritative source of vulnerabilities that have been exploited in the wild. The KEV catalog is maintained by the Cybersecurity & Infrastructure Security Agency (CISA) of the US Department of Homeland Security.
Prioritization of CVEs
To reduce overload, Panoptica automatically prioritizes the expansive list of vulnerabilities found in your environment. This enables you to focus on the CVEs that matter most, reducing the effort required to review and mitigate the vulnerabilities that will have the most impact on improving your security posture.
For example, in the image below, filtering for prioritized vulnerabilities narrows a list of over 5,000 CVEs to just 268 vulnerabilities.
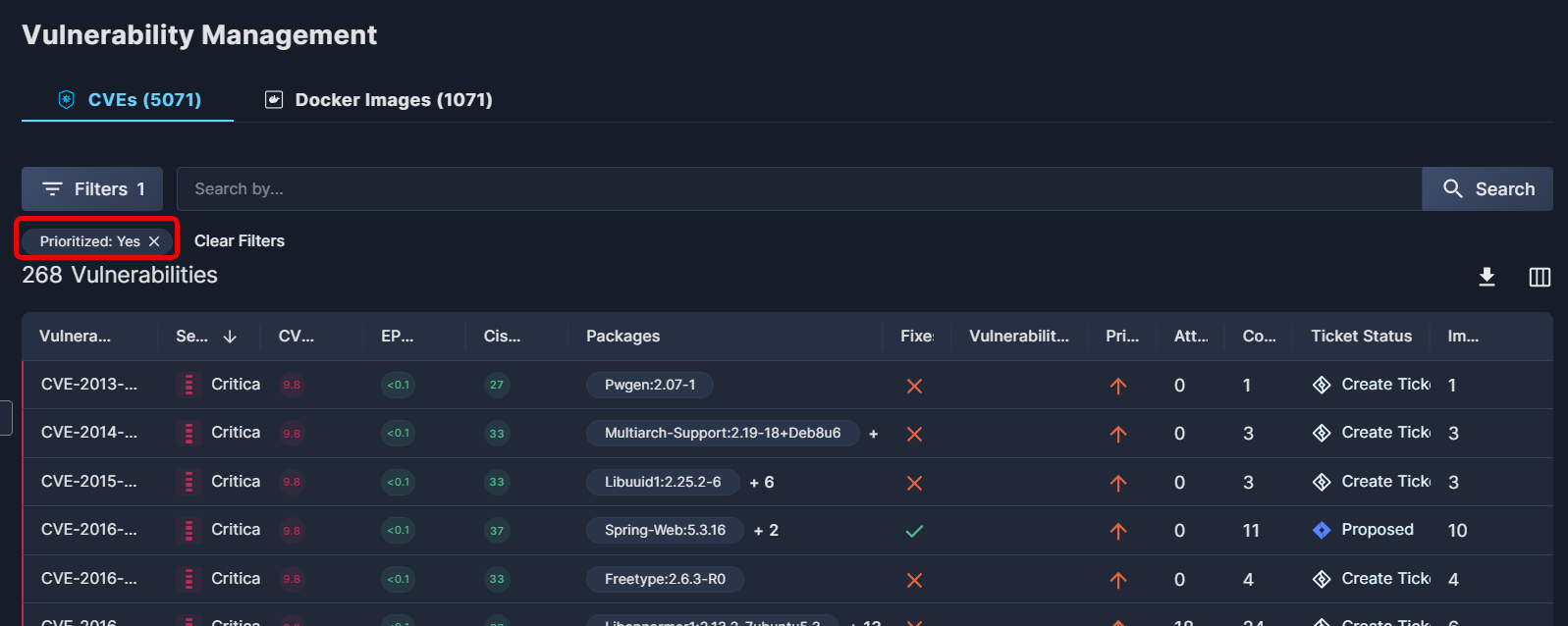
How Does Prioritization Work?
The vulnerabilities are prioritized by a combination of CVSS scores, exploitability, attack vectors, location, and more:
- Any vulnerability publicly exposed and detected by a network scanner.
- Any exploitable vulnerability with a network-based attack vector, which resides in a public asset.
- Any vulnerability with a network-based attack vector and a CVSS score higher than 8, which resides in a public asset.
- Any vulnerability with a local-based attack vector and a CVSS score higher than 8, which is related to a potential detected attack path.
- Any vulnerability with a CVSS score higher than 9, which does not require a physical attack vector.
Updated 4 months ago
