Built-in System Rules
Panoptica's Policy Management feature provides visibility into hundreds of system rules built into the Panoptica platform. Viewing the built-in rules provides transparency into how Panoptica applies these rules to secure your cloud resources, enabling you to better understand the Panoptica modules they support.
While you cannot edit Panoptica's built-in rules, you can customize their application by assigning them to custom Frameworks and categories that you define.
Posture Risk Rules
Navigate to the Policies tab under Management in the Panoptica console, and click the Posture Risk tab to view these built-in policy rules.
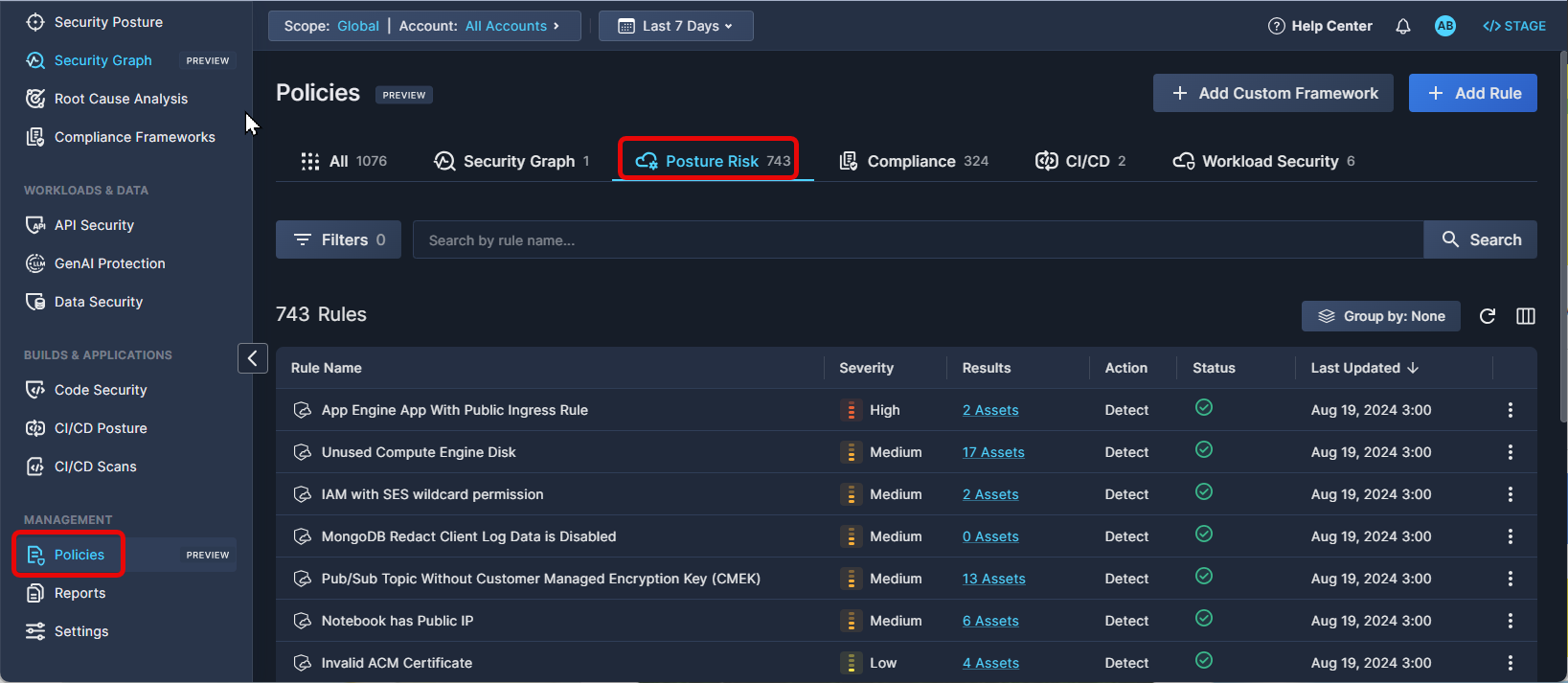
The rules under the Posture Risk engine are looking for misconfigurations in your cloud environment. When a match is found, the engine triggers a risk finding in the Security Posture page.
The posture risk rules are managed by Panoptica's research team. While every match will trigger a Security Posture risk finding, the severity of the findings is based on other considerations, such as any toxic combinations that could comprise an Attack Path.
Posture Risk rules use standard jq syntax, which provides flexibility vis-à-vis JSON files. The query is run against the JSON file of the relevant asset or resource, which can be found on the Asset Inventory page.
You can test Posture Risk rules by copying the rule logic and the JSON of a particular asset, and plugging them into https://jqplay.org/. This could be useful for gaining a better understanding of the rule's purpose and behavior.
More information about jq syntax can be found in the jq 1.7 Manual.
Compliance Rules
Navigate to the Policies tab under Management in the Panoptica console, and click the Compliance tab to view these built-in policy rules.
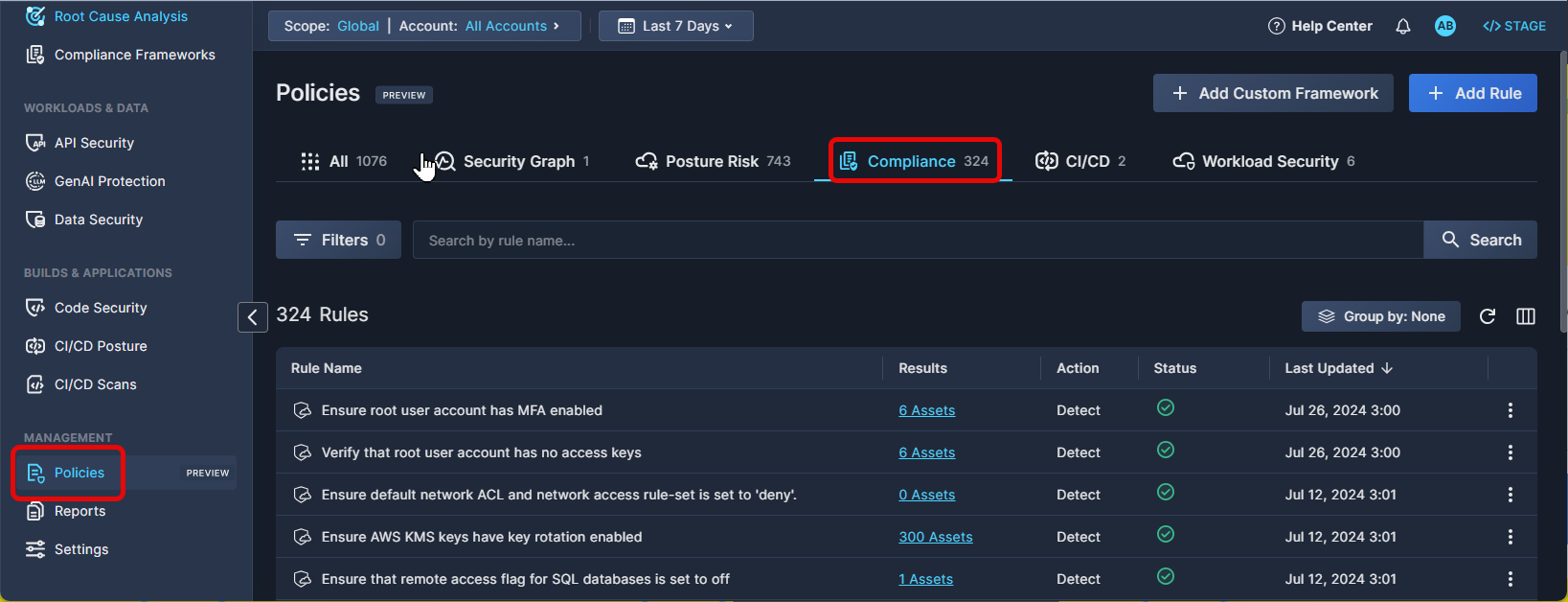
The rules under the Compliance engine run against the configuration of your cloud resources, to ensure that your infrastructure adheres to regulatory, security, and/or organization standards. The results of the compliance rules appear on Panoptica's Compliance Framework page.
Each compliance rule checks whether a specific input file meets the criteria defined in the rule logic. Compliance rules are also maintained by Panoptica engineers, using Rego, the Open Policy Agent's open source query language.
You can test compliance rules using the Rego Playground: https://play.openpolicyagent.org/.
Updated 7 months ago
