Use Cases for Root Cause Analysis
Utilize this new tool to reduce the security team workload and remediate critical issues based on their root cause.
Use case #1: Address an Insecure Template Definition with a high health score impact
Insecure Template Definitions root cause discovers a single template (k8s deployment/k8s daemon set/any other template that creates instances) that has security issues in the template itself. Therefore all those issues are propagated to the template's instances (children), so the template is the same root cause for all issues (findings), and can be remediated by fixing the template.
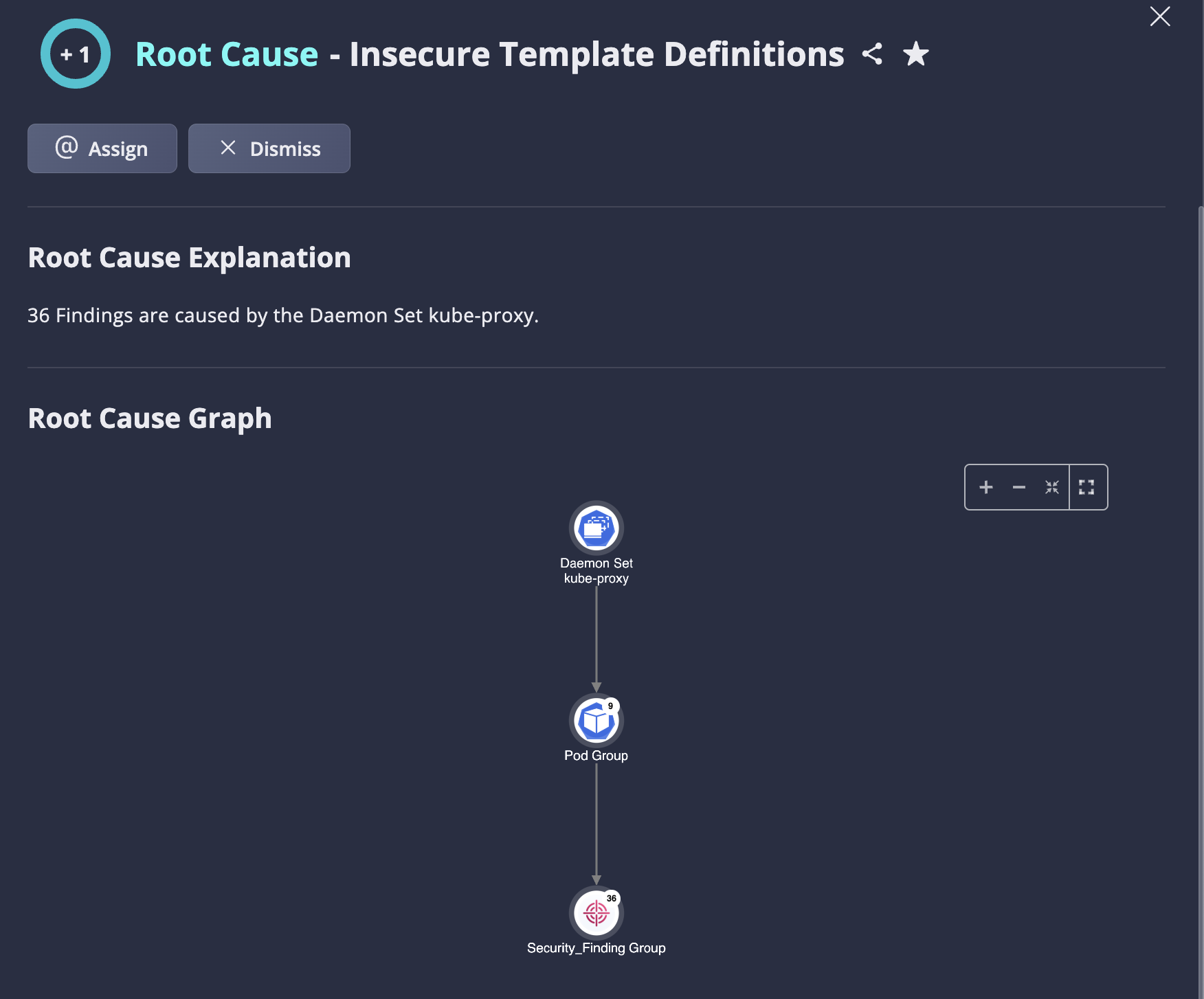
Fig 1. Address an Insecure Template Definition with a high impact on the health score by securing it.
How-to-use:
- Go to Remediation Hub > Filters
- Select Root Cause "Insecure Template Definition"
- Click on the root cause with the highest impact on the health score
- Review the findings
- Assign or Dismiss
- Protip: you can also review the findings' related assets, and ticket status, assign or share the link with a Panoptica user
Use Case #2: Fix a Permissive Identity Object by applying right-size IAM
Permissive Identity Object root cause finds a single identity object, such as AWS IAM Policy or GCP Roles, with permissive access permissions and is connected to multiple other identities, such as Users/Groups/Roles, and gives them this permissive access. The policy/role that gives high permissions to all identities is the same root cause for all issues (findings), which can be remediated by updating the policy/ role, rather than each individual identity.
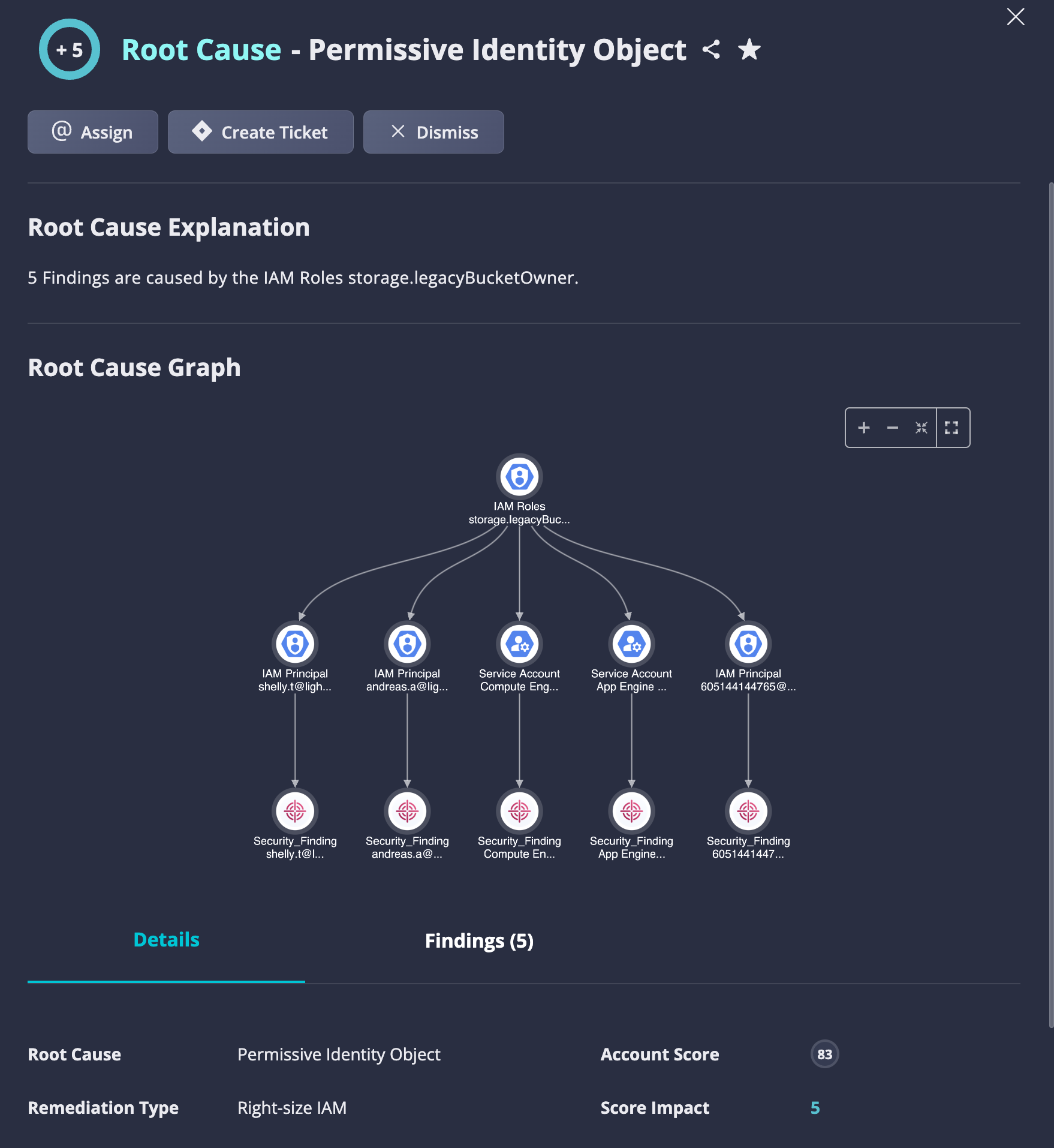
Fig 2. Fix a Permissive Identity Object by applying right-size IAM.
How-to-use:
- Go to Remediation Hub > Filters
- Select Root Cause "Permissive Identity Object"
- Select the root of interest
- Explore the findings
- Assign, Create a Ticket, or Dismiss
Use Case #3: Segregate resources to avoid a Resource Overuse
Excessive use of computing resources such as CPU, memory, storage, and network bandwidth, can lead to performance issues, downtime, and increase costs. To remediate, use Panoptica's recommendations to segregate resources. Review the attack path and remediate the issue using a ready-made Terraform / JSON policy.
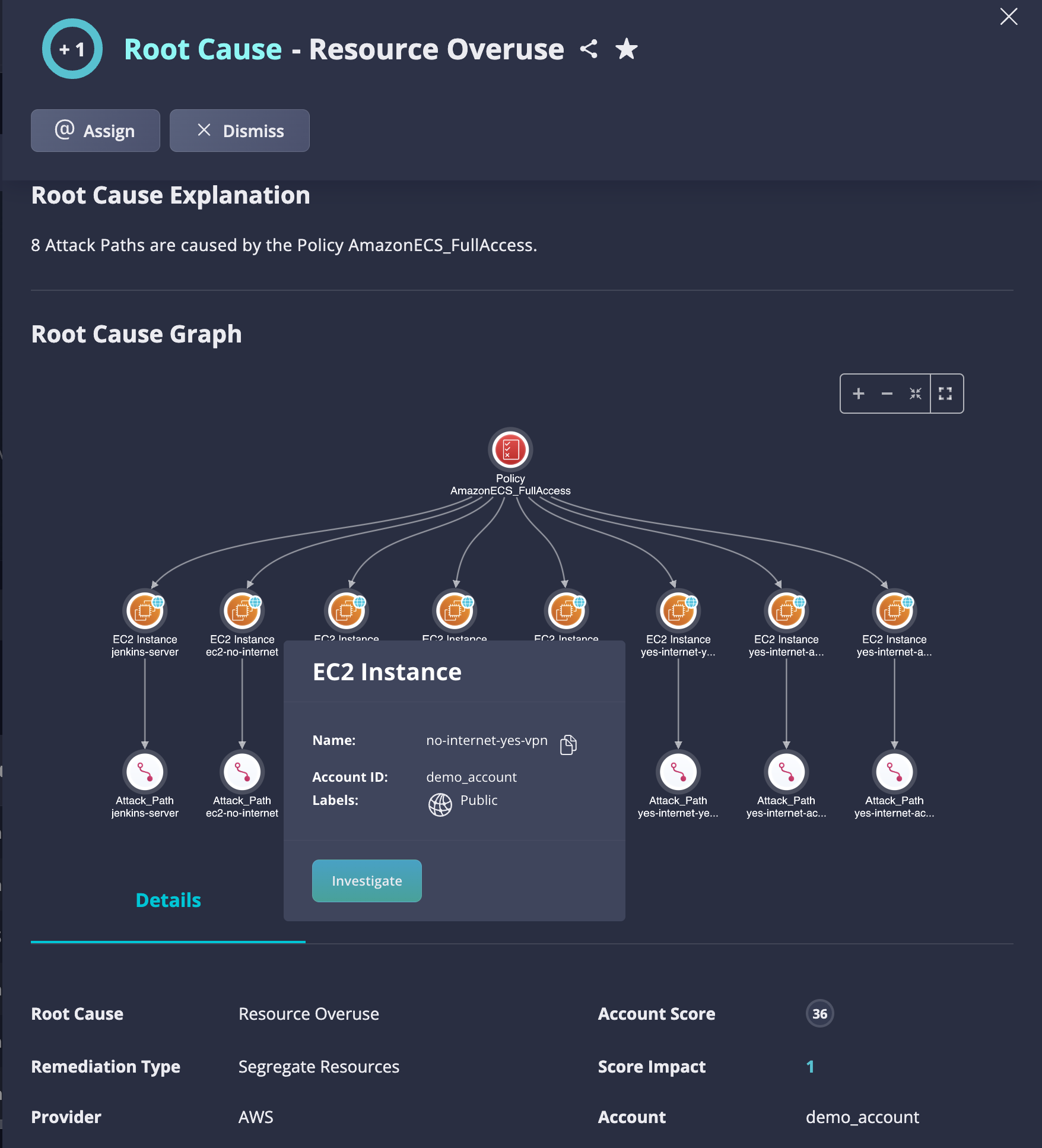
Fig 3. Segregate resources to avoid a Resource Overuse.
How-to-use:
- Go to Remediation Hub > Filters
- Select the Root Cause "Resource Overuse"
- Select a root cause to investigate
- Click "Investigate" and review the attack paths related to the resources
- Remediate Assign or Dismiss
Use Case #4: Fix a permissive network access by restricting network access
Permissive Identity Object root cause finds a single identity object, such as AWS IAM Policy or GCP Roles, with permissive access permissions and is connected to multiple other identities, such as Users/Groups/Roles, and gives them this permissive access. The policy/role that gives high permissions to all identities is the same root cause for all issues (findings), which can be remediated by updating the policy/ role, rather than each individual identity.
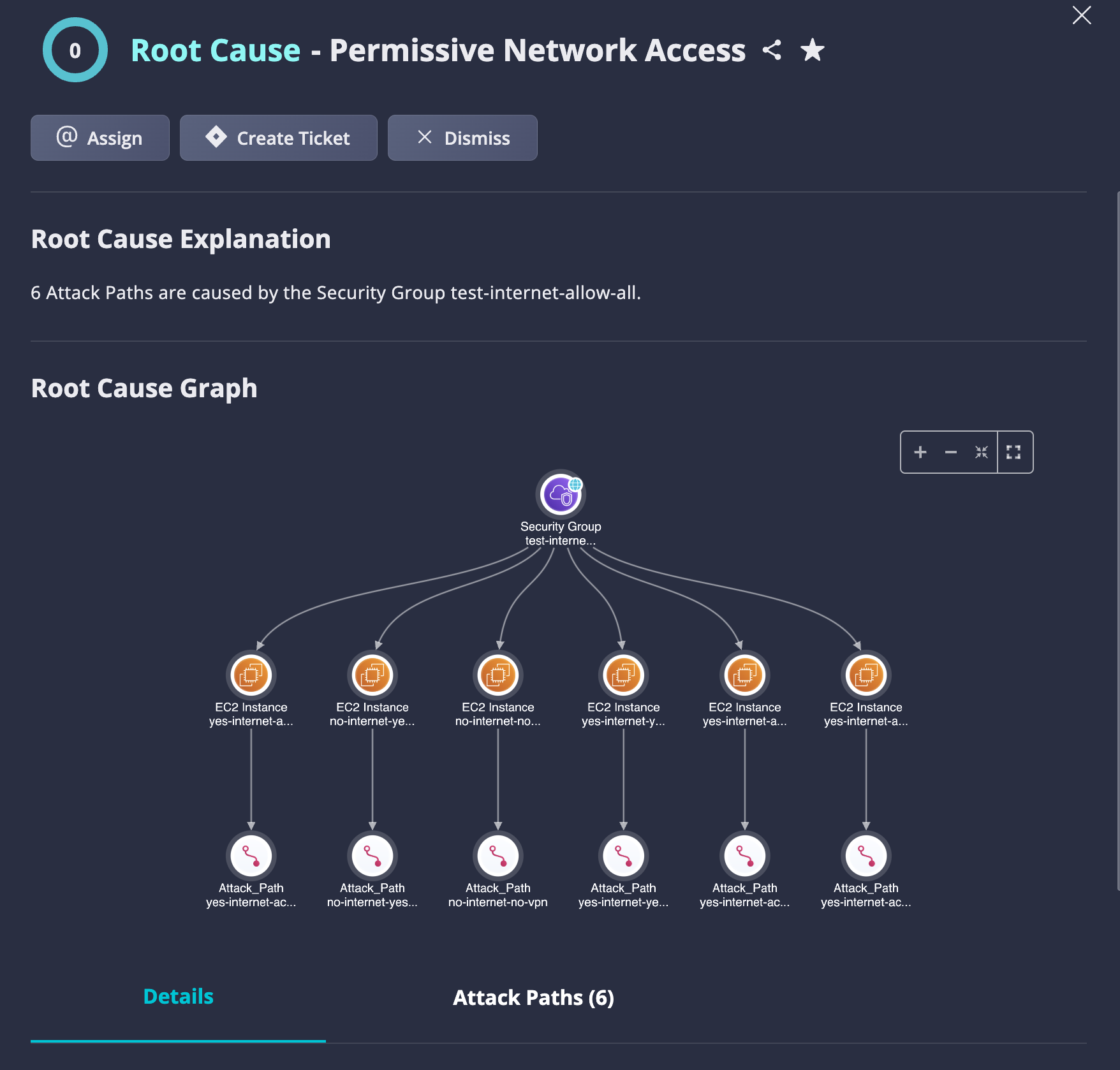
Fig 4. Fix a permissive network access by restricting network access.
How-to-use:
- Go to Remediation Hub > Filters
- Select the Root Cause "Permissive Network Access"
- Click on the root cause
- Review the attack paths related to the security group
- Investigate > Remediate or Assign or Dismiss
Use Case #5: Patch a vulnerable image
Unpatched Image root cause reveals an image (can be compute Image such as AMI or docker image) that comes with vulnerabilities. Therefore, all compute assets or containers that use the vulnerable Image has all vulnerabilities as well. The vulnerable Image is the same root cause for all issues (vulnerabilities) which can be remediated by updating it with the latest security patches.
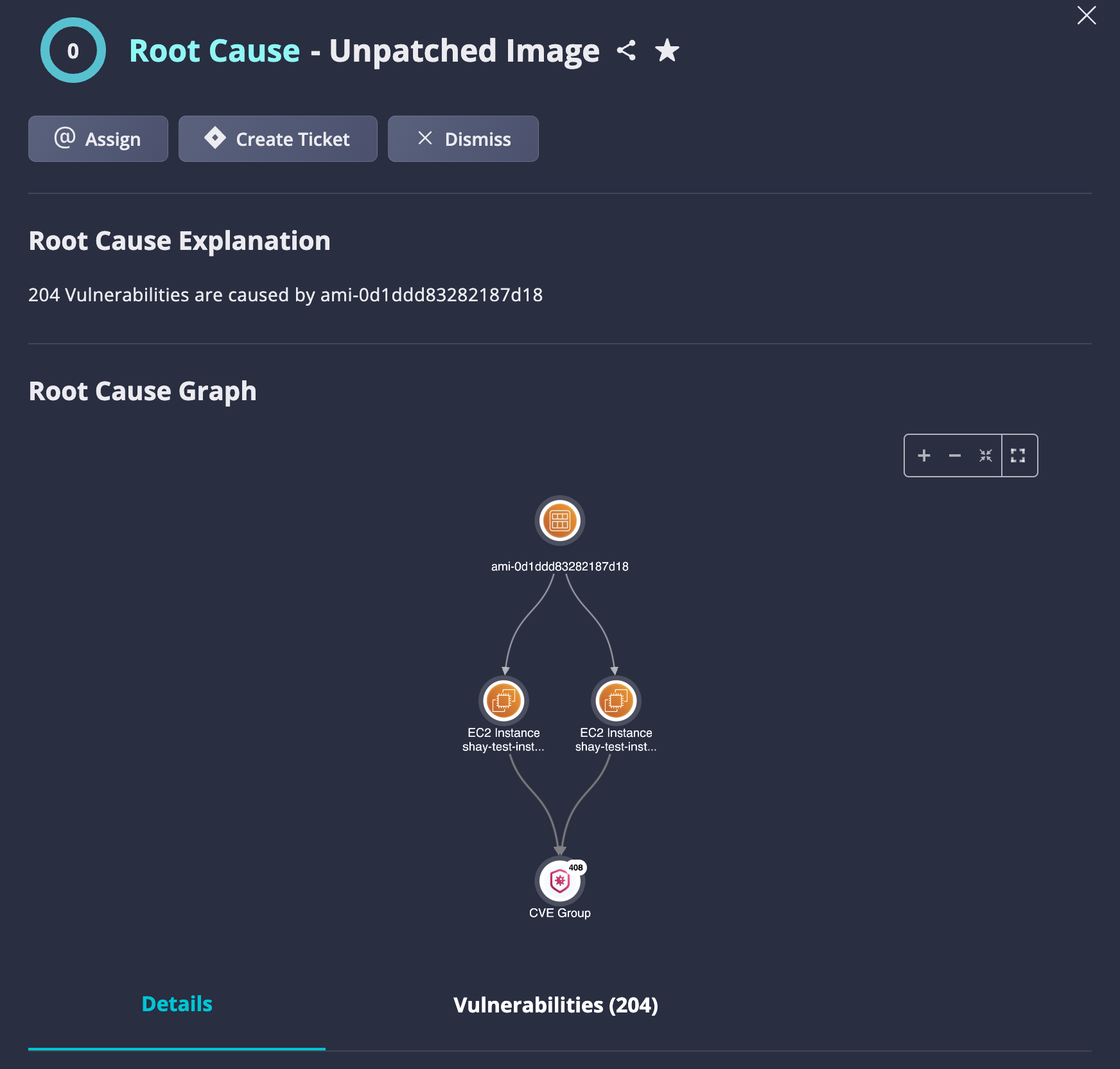
Fig 5. Patch a vulnerable image.
How-to-use:
- Go to Remediation Hub > Filters
- Select Root Cause "Unpatched Images"
- Click on one of the root causes
- Review findings
- Remediate, Assign, or Dismiss
Use Case #6: Secure a Secret
Insecure Secret Store root cause locates a single secret value found as cleartext on multiple different assets; the secret itself is the root cause for all findings, which can be remediated by securing the single secret.
How-to-use:
- Go to Remediation Hub > Filters
- Select Root Cause "Insecure Secret Store"
- Click on one of the root causes
- Review findings
- Secure the secret, Assign or Dismiss
Updated over 1 year ago
