CVEs Prioritization
Overview
Panoptica scans for vulnerabilities using different tools and threat intelligence feeds, including:
- AWS EC2 disk scanning
- K8s image scanning
- Intsights - vulnerabilities and darknet threat intelligence
- Shodan - public assets network scanner
- Spyse - public assets threat intelligence
Prioritization of CVEs
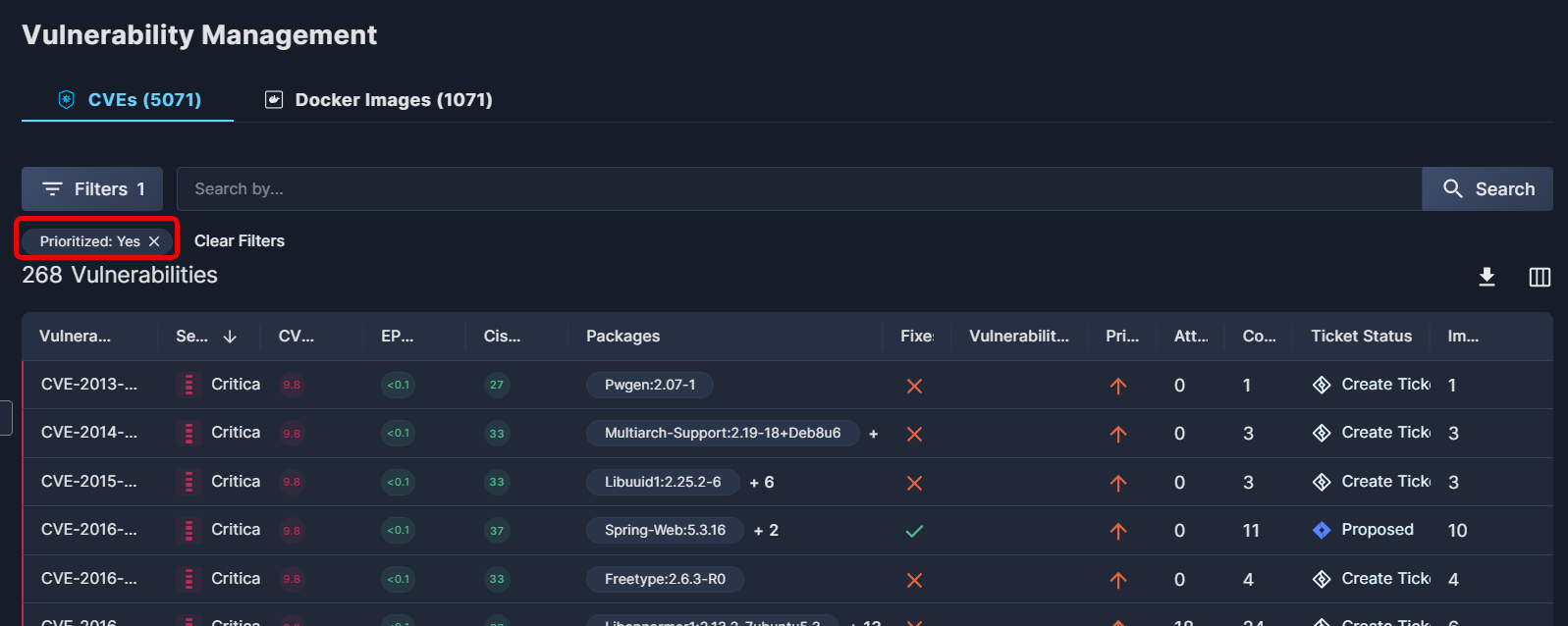
To reduce overload, Panoptica prioritizes the expansive list of vulnerabilities found in your environment. This enables you to focus on the CVEs that matter most, reducing the effort required to review and mitigate the vulnerabilities that will have the most impact on improving your security posture.
In the example below, Panoptica detected over 5,000 CVEs, but after filtering for prioritized vulnerabilities, that is reduced to just 268 vulnerabilities.
How Does Prioritization Work?
The vulnerabilities are prioritized by the following logic:
- Any vulnerability publicly exposed and detected by a network scanner.
- Any exploitable vulnerability with a network-based attack vector, which resides in a public asset.
- Any vulnerability with a network-based attack vector and a CVSS score higher than 8, which resides in a public asset.
- Any vulnerability with a local-based attack vector and a CVSS score higher than 8, which is related to a potential detected attack path.
- Any vulnerability with a CVSS score higher than 9, which does not require a physical attack vector.
Updated about 2 months ago
