Policy Rules
Panoptica's Policies tab is pre-loaded with hundreds of rules from across Panoptica's modules, exposing the built-in rules that Panoptica uses to secure your resources out-of-the-box. In addition to providing visibility into Panoptica's Security Posture and Compliance rules, this also enables you to identify updates, by sorting the table according to the Last Updated field.
While you cannot edit the built-in system rules, you can customize their application by assigning them to custom Policy Frameworks and categories that you define.
You can also create or edit your own rules, to fit your needs. Custom rules appear alongside built-in rules in the Policies tab as well.
View Rules
Navigate to the Policies tab under Management in the Panoptica console to view Panoptica's built-in policies, and start generating your own.
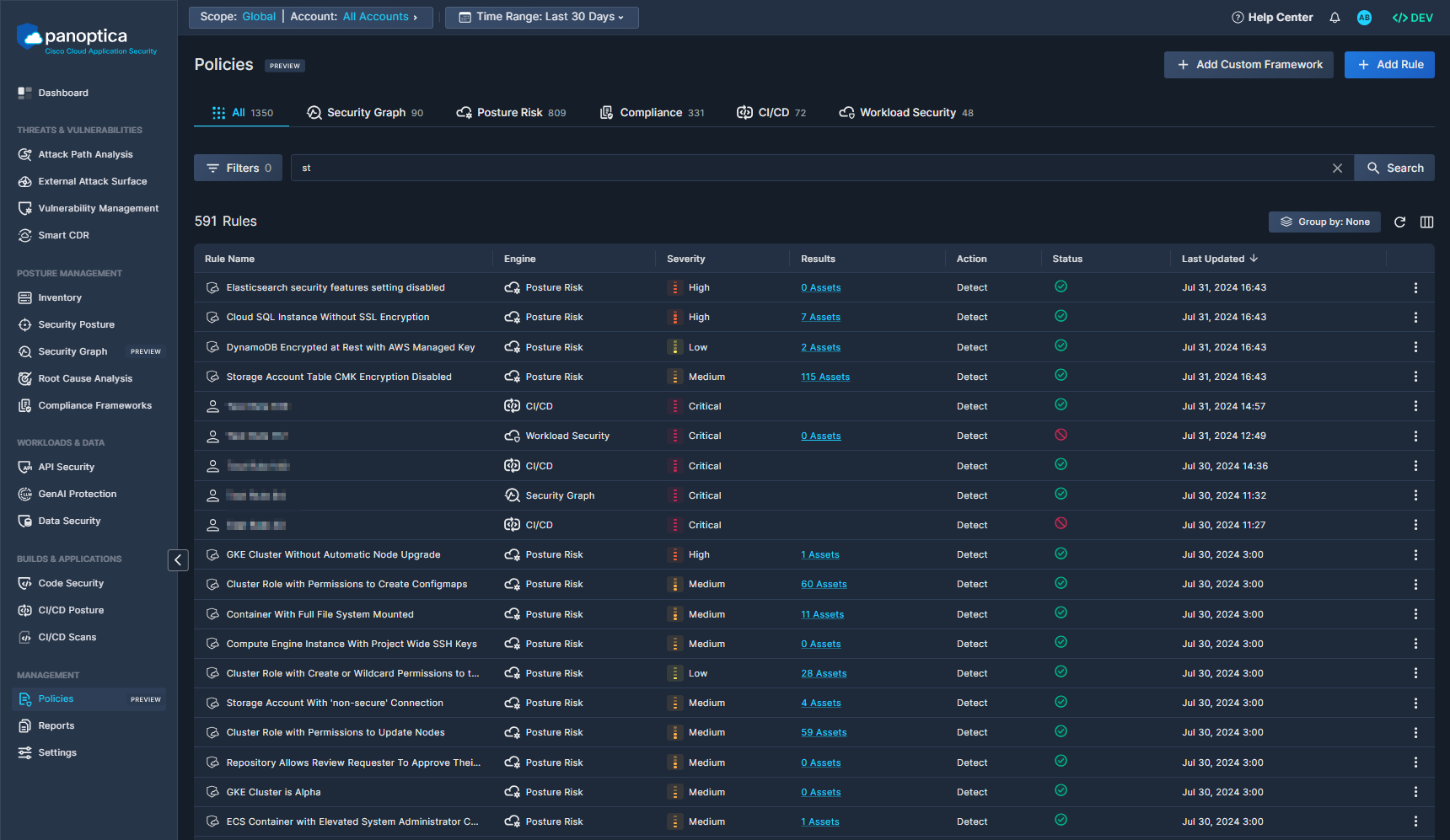
The default view displays all of the rules available in a unified list. Select one of the other tabs to filter the list by one of the specific rule engines: Security Graph, Posture Risk, Compliance, CI/CD, or Workload Security. The number beside each title indicates the number of rules in that engine.
You can further refine the results using predefined filters and open search.
- Use the drop-down Filters option to narrow the results by: Engine, Severity, Status, and Frameworks & Categories.
- Use the Search bar to look for a text string in a rule name. To clear the search, click the ×.
You'll find a few icons in the upper right corner of the table for managing the list:
- Click the Grouped by button to aggregate the list by Framework.
- Click the circle-arrow icon (↻) to Reload the table, without the need to refresh the whole page.
- Select which columns are displayed, and in which order, by clicking the Arrange Columns button (▥).
Rule Properties
The columns in the Rules table display the following summary information about each rule:
- Rule Name
A short textual name given to a rule, which must be unique across your environment. The table can be sorted alphabetically by Rule Name. - Engine
The backend mechanism responsible for detecting and enforcing each set of policy rules. - Severity
The severity of the rule’s results. The table can be sorted by this field. - Results
The number of matching results for the rule.
Click on the Results value to list the results when relevant. See Rule Results below for details. - Action
The action Panoptica performs once the rule logic is triggered, such as Detect or Block. - Status
Whether a policy rule is enabled or disabled. Disabled rules can be viewed, but are not executed. - Last Updated
The date and time that the policy rule was updated. The table can be sorted by this field.
Click the three dots (⁝) at the end of any row in the table to open a drop-down list of actions you can perform on that rule.
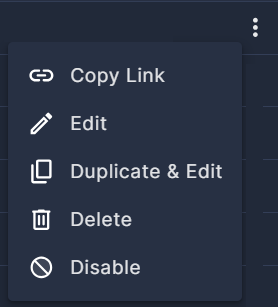
- Copy Link is useful for sharing the rule details with others in your team.
- Edit enables you to view the rule details, and make changes when possible. Options are limited when editing built-in rules, but this is where you can associate them to your custom frameworks.
Frameworks and Rules
A single rule – whether built-in or custom – can be associated with more than one custom framework.
You are only allowed to attach/detach rules to custom frameworks, as the built-in frameworks are pre-defined by the Panoptica team.
- Duplicate and Edit enables you to copy a custom rule and create a new rule based on the original. This is useful for creating multiple rules with similar traits.
- You can Delete your own rules, but it will be grayed-out for built-in Panoptica rules.
- Similarly, you can Disable your own rules, but only some built-in rules.
Rule Details
When you click the three dots (⁝) at the end of a row and select Edit, you will reach the Rule details view. Note that simply clicking on a row in the Rules table may open the same view, depending on the type of rule you're looking at. Some rules behave differently, though, which is why the Edit option is recommended.
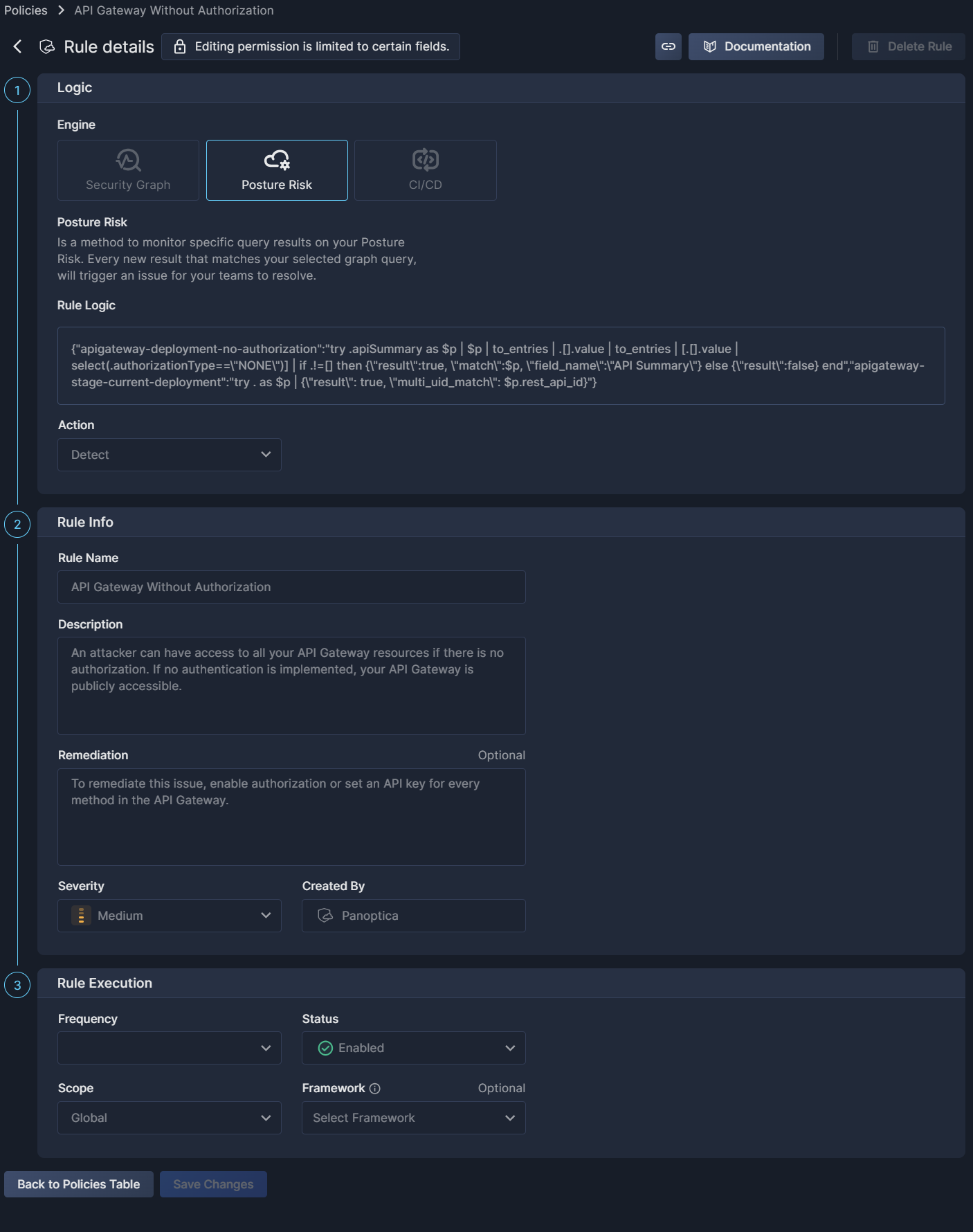
The Rule details view is made up of three sections:
- Rule Logic: the conditions that trigger the rule. For your own custom rules, you'll see the logic you defined when creating the rule. For system rules, like Posture Risk or Compliance, you'll see the query logic in common syntax, as defined by Panoptica's engineers. For details, see:
- Rule Info: additional details, including remediation information (when available) and severity.
- Rule Execution: how the rule behaves when triggered.
Rule Results
Viewing the rule results varies with the different rule engines. The results of some rule engines appear in other modules in the Panoptica console UI, whereas some are viewable via the Policies tab.
Posture Risk
Posture Risk rules are used to generate Security Posture findings. To view the results of a particular Posture Risk rule in the Policies table, click the link in the Results column. This will open a new browser tab displaying the Security Posture findings triggered by that rule.
Workload Security
Workload Security rules can detect vulnerabilities and security findings in your Kubernetes workloads, as well as block pods that could pose a risk to your environment. To view the results of a particular Workload Security rule in the Policies table, click the link the the Results column. This will open a side drawer listing details about the rule results.
See Workload Security Rules for details.
Create Custom Rules
You can create your own rules in Panoptica to gain visibility into your organization's policies or compliance by utilizing environment parameters like tags and naming conventions. Custom rules appear alongside built-in rules in the Policies tab as well.
Permissions required
Users must have an Owner or Ops role in Panoptica to create custom rules.
An Ops user can edit/delete custom rules that they created; an Owner can edit/delete any custom rule in your tenant. Panoptica system rules cannot be edited or deleted.
See User Management for details on User Roles.
Click the + Add Rule button at the top of the Policies tab to start building your own custom policy rules, with actions, conditions, and operators.
The Add Rule dialog box is where you define the rule logic, provide details about the rule, and define how and when it is executed.
Select the Panoptica engine on which you want to base your custom rule:
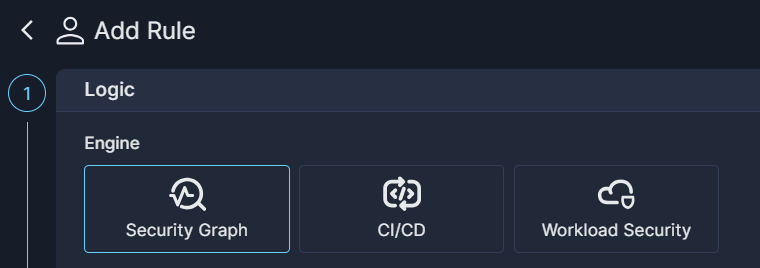
Security Graph: The rule logic for the Security Graph engine is based on the Query Builder at the heart of the Security Graph feature. You can create custom rules that integrate your assets with security insights from across Panoptica's modules: CSPM, KSPM, API Security, and more. By adding advanced filters and relationship mapping between assets, you can customize rules on which to build your policies. See Security Graph Rules for details.
CI/CD: Use the CI/CD engine to define custom rules that monitor you code base for potential risks. By setting conditions for those findings, you can enforce custom policies, prioritize vulnerabilities, and effectively assess risks to your software development lifecycle. See CI/CD Rules for details.
Workload Security: Use the Workload Security engine to define custom rules that can help you identify vulnerabilities and security findings in your Kubernetes workloads in realtime. In addition to detecting events, you can also configure the rules to block pods that could pose a risk, to ensure continuous protection and security compliance for your environment. See Workload Security Rules for details.
Scope and Rules
Note that policy rules are filtered by scope. If you create a rule in the Global scope, it will not be visible if you set the Top Bar Filter to another scope, and vice versa.
See Scope Management for details on defining scopes.
Updated 7 months ago
